Bare Metal Server
This section introduces the key concepts of the Bare Metal Server service.
Instance
An instance in Bare Metal Server is a dedicated physical server that is not virtualized and runs an operating system and related software directly. This instance can have various statuses, including operational and task statuses, which users can check to perform management actions.
Instance type
Bare Metal Server instances allow applications to directly access the server's processor and memory. They are suitable for workloads that require a non-virtualized environment or use of a custom hypervisor. Unlike general-purpose instances, these occupy an entire physical server within the cloud, ensuring high performance and stability.
Instance types offered by KakaoCloud include Memory optimized and Accelerated computing types, with more to be added in the future. For more information on instance types and pricing, refer to Bare Metal Server pricing on the official KakaoCloud website.
General purpose instances will be supported in the Bare Metal Server service in the future.
Instance lifecycle
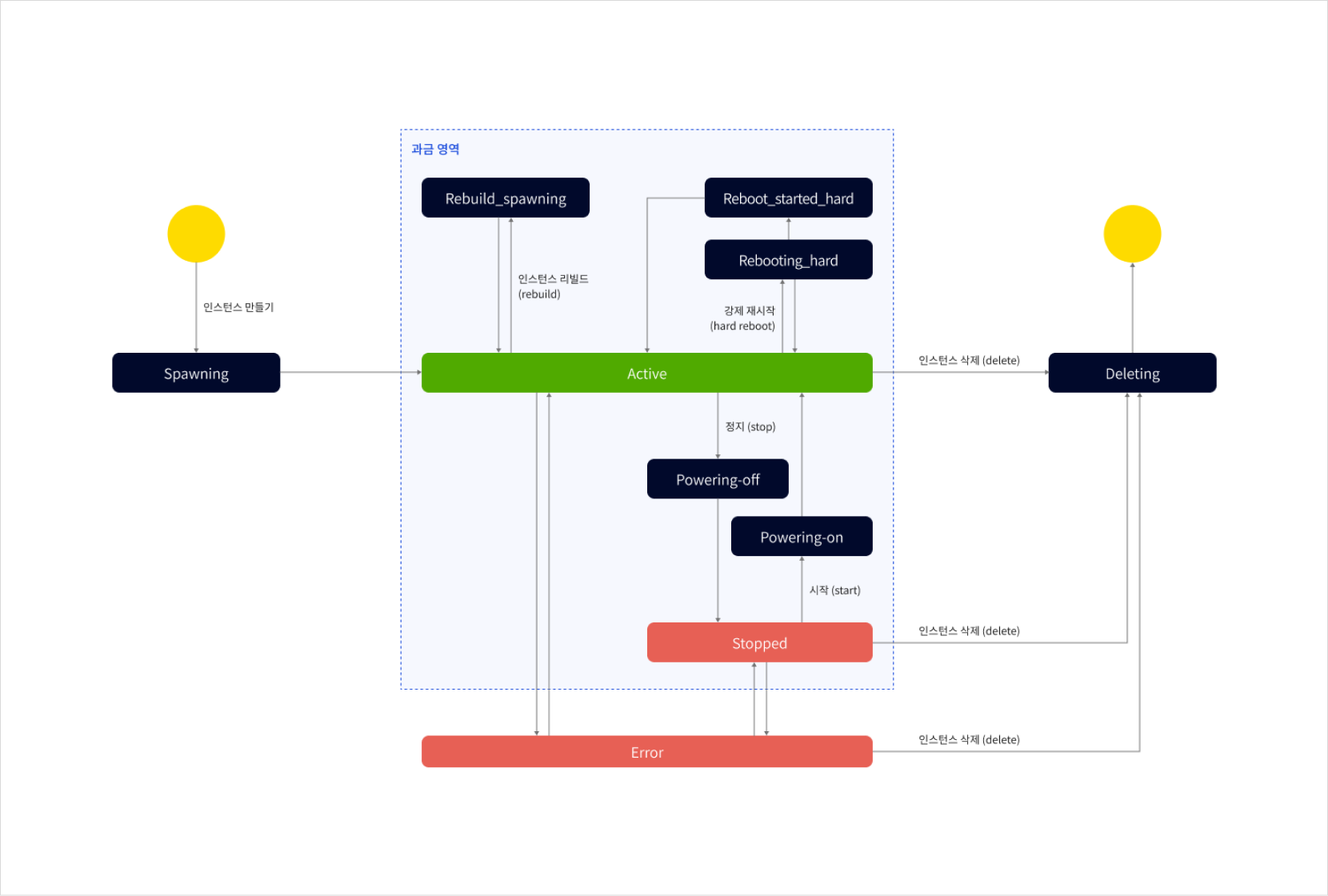
Instances go through various statuses from creation to termination, which can be checked through their lifecycle states. Users can utilize these statuses for operational management. The lifecycle stages provided by Bare Metal Server are as follows:
| Category | Name | Description | Billing |
|---|---|---|---|
| Command | Start | Start the instance | - |
| Stop | Stop the instance | - | |
| Terminate | Instance is running and available | - | |
| Hard reboot | Forcefully restart the instance | - | |
| Rebuild | Reinstall OS image and reset key pair | - | |
| Delete | Permanently delete the instance | - | |
| Instance state | Spawning | Instance is being created | No |
Active | Instance is running | Yes | |
Stopped | Instance is stopped but resources remain allocated on the hypervisor | Yes | |
Rebuild_spawning | Instance is being rebuilt | Yes | |
Rebooting_hard | Hard reboot initiated | Yes | |
Rebooting_started_hard | Hard reboot in progress | Yes | |
Powering-off | Instance is shutting down | Yes | |
Powering-on | Restarting a stopped instance | Yes | |
Error | Instance encountered an error and is unusable | No | |
Deleting | Instance is being deleted | No |
Instance state and billing
| Category | Name | Description | Billing |
|---|---|---|---|
| Instance state | Spawning | Instance is being created | No |
Active | Instance is running | Yes | |
Stopped | Instance is stopped but resources remain allocated on the hypervisor | Yes | |
Rebuild_spawning | Instance is being rebuilt | Yes | |
Rebooting_hard | Hard reboot initiated | Yes | |
Rebooting_started_hard | Hard reboot in progress | Yes | |
Powering-off | Instance is shutting down | Yes | |
Powering-on | Restarting a stopped instance | Yes | |
Error | Instance encountered an error and is unusable | No | |
Deleting | Instance is being deleted | No |
Image
You can launch an instance by selecting an operating system (OS) and applications according to your use case.
In the KakaoCloud Bare Metal Server service, users cannot create or manage their own images. Only default images provided by KakaoCloud are available.
Default images available
| Category | Image type |
|---|---|
| Linux | Ubuntu 20.04 |
| Ubuntu 20.04 (GPU) | |
| Ubuntu 22.04 | |
| Ubuntu 22.04 (GPU) | |
| CentOS Stream 8 | |
| Rocky Linux 8 | |
| Rocky Linux 9 | |
| Alma Linux 9 | |
| Windows | Windows 2019 |
| Windows 2022 |
As of November 2024, Windows images in the Bare Metal Server service are only available for use with r2a.baremetal.
Key pair
A key pair is a cryptographic key pair used for secure communication and authentication between the cloud environment and instances or virtual machines. A key pair consists of a public key and a private key.
-
Public key: The public key can be shared with others or systems. It is used to encrypt data when connecting to an instance. The instance uses the corresponding private key to decrypt the data.
-
Private key: The private key is paired with the public key and must be kept secure. Only the owner should have access to it. It is used to connect to instances, decrypt data, or authenticate access.
Network
All Bare Metal Server instances are provided within a VPC environment. Based on your networking requirements, you can build logically isolated service environments. For more details, refer to VPC.
IAM-based role management
The Bare Metal Server service uses IAM-based Role-Based Access Control (RBAC). All resources are created and managed within a project. Users with Project Admin or Project Member roles can create and manage all resources under the project. However, only the owner of a key pair can delete it.
| Role permissions | Project Admin | Project Member | Project Reader |
|---|---|---|---|
| Manage project members | ✓ | ||
| Configure public IP | ✓ | ||
| Manage instances | ✓ | ✓ | △ (view only) |
| Volumes | ✓ | ✓ | △ (view only) |
| Images | ✓ | ✓ | △ (view only) |
| Key pairs | ✓ | ✓ | △ (view only) |