Manage network
Here is how to manage network settings in the Bare Metal Server service.
Associate public IP
You can associate a public IP with an instance.
Only Project Admin can associate public IPs.
-
Go to the KakaoCloud console > Beyond compute service > Bare metal server menu.
-
In the Instance menu, select the [More] icon on the instance to associate a public IP, then select Associate public IP.
-
In the Associate public IP pop-up, review the information, select a public IP to assign, and select [OK].
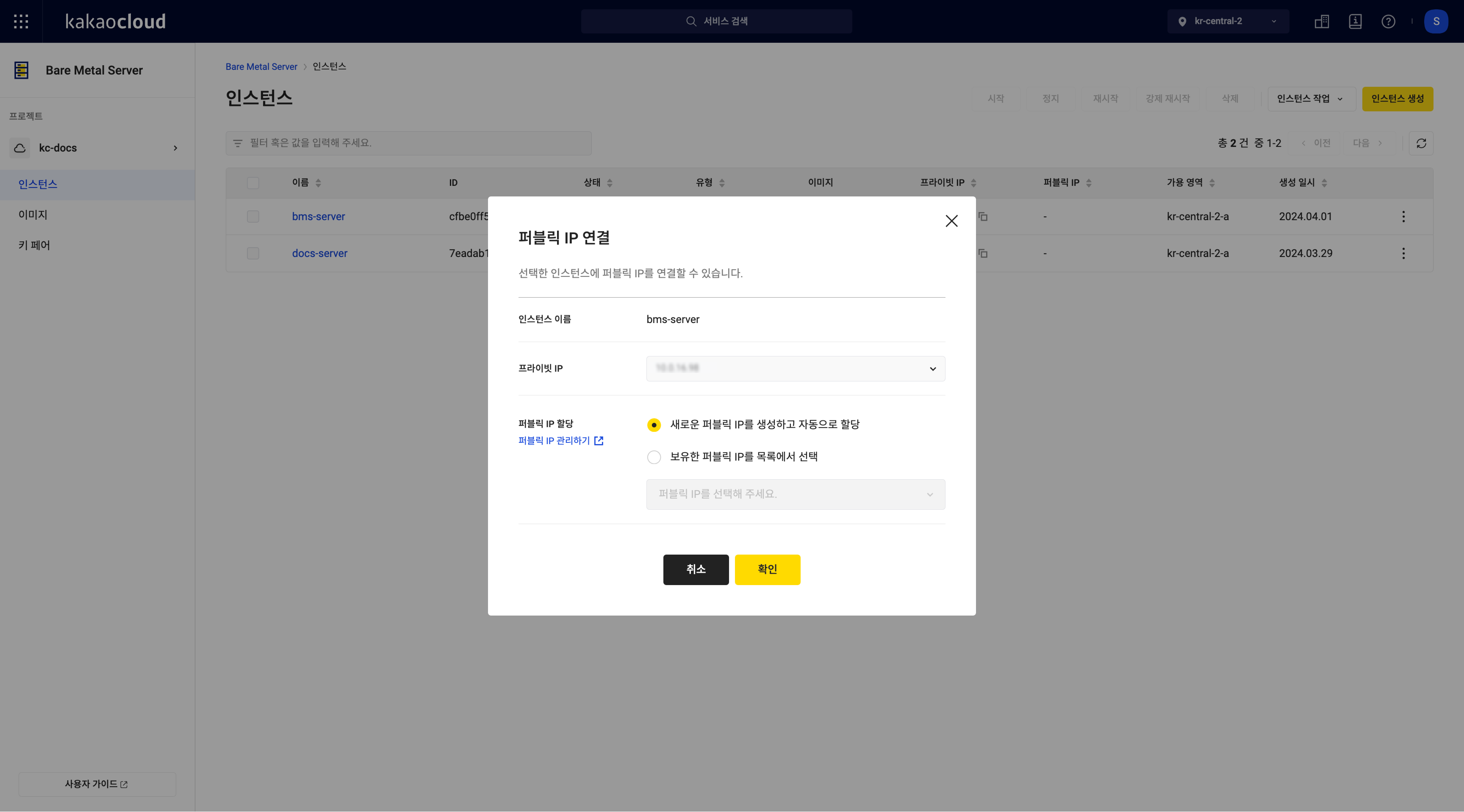 Associate public IP
Associate public IP
Disassociate public IP
You can disassociate a public IP from an instance.
Only Project Admin can associate and disassociate public IPs.
If you only disassociate the public IP without deleting it, the resource is not released and charges will continue to accrue even if the instance is not in use.
- Go to the KakaoCloud console > Beyond compute service > Bare metal server menu.
- In the Instance menu, select the [More] icon on the instance to disassociate a public IP, then select Disassociate public IP.
- In the Disassociate public IP pop-up, review the information and select Automatically delete the disassociated public IP.
- Select [Disassociate].
When using multi-network interface
Bare Metal Server instances support multiple network interfaces per instance, but we do not recommend this configuration due to potential network routing issues.
If more than one network interface is connected to the same subnet, problems such as asymmetric routing may occur. Therefore, we recommend configuring each interface to connect to a different subnet.
If you must connect multiple interfaces to the same subnet, additional configuration is required. You must remove default gateways from interfaces that are not used for external communication.
Execute all commands with sudo using root privileges.
-
Run the following command to check the routing table:
Check instance routing configurationsudo route -nExample output:
Example routing tableDestination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 198.168.0.1 0.0.0.0 UG 100 0 0 eth0
0.0.0.0 10.10.0.1 0.0.0.0 UG 100 0 0 eth1
198.168.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
10.10.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1 -
Keep the gateway connected to the interface used for external communication and delete others:
Delete gateway for eth1sudo route del default gw 10.10.0.1 dev eth1Resulting routing table:
Routing table after deletionDestination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 198.168.0.1 0.0.0.0 UG 100 0 0 eth0
198.168.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
10.10.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
Configure iptables
iptables is a firewall table on Linux used by system administrators to define packet filtering policies.
Until security groups are supported, users must configure firewall policies directly within their OS using iptables.
For more about iptables, refer to the Netfilter iptables project.
Terminology and commands
Basic terms
| Term | Description |
|---|---|
| Target | Action taken when a rule is matched - ACCEPT: Allow the packet - DROP: Block without error message - REJECT: Block with error message |
| Chain | Rule group applied to different traffic directions - INPUT: Incoming packets - OUTPUT: Outgoing packets - FORWARD: Packets being routed |
Full commands
| Option | Description |
|---|---|
| -A (–append) | Append new rule |
| -D (–delete) | Delete rule |
| -C (–check) | Test packet against rule |
| -R (–replace) | Replace with new rule |
| -I (–insert) | Insert rule before existing |
| -L (–list) | List rules |
| -S (–list-rules) | Output all rules |
| -F (–flush) | Delete all rules in a chain |
| -Z (–zero) | Reset counters |
| -N (–new) | Create new chain |
| -X (–delete-chain) | Delete chain |
| -P (–policy) | Set default policy |
| -s | Source IP |
| -d | Destination IP |
| --sport | Source port |
| --dport | Destination port |
| -j | Jump target |
| -p | Protocol (e.g. TCP, UDP, ICMP) |
| -i | Input interface |
| -o | Output interface |
| -t | Table type (filter, nat, mangle); default: filter |
Configure policy
KakaoCloud’s Bare Metal Server images come with iptables v1.6.1 and SSHGUARD preinstalled.
SSHGUARD protects against brute force attacks (e.g., multiple failed login attempts). It does not replace iptables, and users must define rules based on their own security needs.
For more about SSHGUARD, refer to the SSHGUARD official site.
Check iptables version
sudo iptables -V
iptables v1.6.1
View current rules
sudo iptables -nL --line-numbers --verbose
Chain INPUT (policy ACCEPT 451 packets, 44136 bytes)
num pkts bytes target prot opt in out source destination
1 773 77557 sshguard all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
Chain OUTPUT (policy ACCEPT 278 packets, 30411 bytes)
Chain sshguard (1 references)
Output all rules
You can output all rules.
The output is formatted in a way that is directly reusable, as it follows the iptables-save format, which differs from the output of the sudo iptables -L command.
sudo iptables -S -v
-P INPUT ACCEPT -c 511 50127
-P FORWARD ACCEPT -c 0 0
-P OUTPUT ACCEPT -c 323 36247
-N sshguard
-A INPUT -c 833 83548 -j sshguard
Create rule
When defining iptables rules, be careful not to block essential ports (e.g., SSH or service ports).
KakaoCloud is not responsible for issues caused by user-defined iptables policies. In such cases, you must reinstall the image using the Rebuild feature under [More options].
sudo iptables -A
Examples:
# Allow all traffic on localhost
sudo iptables -A INPUT -i lo -j ACCEPT
# Allow external access on TCP port 22
sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT
# Allow external access on TCP port 80
sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPT
# Allow external access on TCP port 443
sudo iptables -A INPUT -p tcp --dport 443 -j ACCEPT
# Allow access from any source to specific server port
sudo iptables -A INPUT -d 000.000.00.00 -p tcp --dport 22 -j ACCEPT
Delete rule
sudo iptables -D
Examples:
# Delete rule number 4 in INPUT chain
sudo iptables -D INPUT 4
# Delete TCP port 22 reject rule
sudo iptables -D INPUT -p tcp -m tcp --dport 22 -j REJECT
# Delete TCP port 443 accept rule
sudo iptables -D INPUT -p tcp --dport 443 -j ACCEPT
Save rule settings
iptables rules are not persistent after reboot. Save them to /etc/iptables.rules.
sudo iptables-save
sudo cat /etc/iptables.rules
Example output:
filter
:INPUT ACCEPT [1438:151829]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [845:93350]
:sshguard - [0:0]
-A INPUT -j sshguard
COMMIT
Explanation of example rules
| Base command | Option | Chain | Source IP | Destination IP | Protocol | Port | Match | Action |
|---|---|---|---|---|---|---|---|---|
| iptables | -A | INPUT | -s | -d | -p | --dport | -j | ACCEPT |
| iptables | -D | OUTPUT | -s | -d | -p | --dport | -j | DROP |
| iptables | -I | FORWARD | -s | -d | -p | --dport | -j | REJECT |