Key Concepts
Instance
An instance is a virtualized hardware resource, generally referring to a virtual machine that includes computing power, memory, storage space, and networking capabilities. This virtual environment allows users to scale resources up or down as needed, significantly reducing the cost and overhead of managing physical hardware.
Virtual Machine (VM) instances are used to create virtual computers in cloud computing environments, and costs are typically charged based on usage. Cloud computing services virtualize physical server resources to run multiple independent virtual machines simultaneously, improving efficiency and scalability by allowing users to operate multiple VMs on a single physical server.
Each VM instance is typically allocated resources such as CPU, memory, storage, and a network interface. These resources are key determinants of the VM's performance and capacity, and they can be adjusted according to user needs. This allows users to select the most appropriate instance type and size for their applications and services.
| Resource | Description |
|---|---|
| CPU | Virtual CPUs are allocated to the instance, using part or all of a physical CPU |
| Memory | Virtual memory is allocated to the instance, operating with part or all of physical memory |
| Storage | Each instance uses virtual block storage, efficiently distributing physical disk space |
| Network interface | A virtual primary network interface is attached to each instance for communication |
Instance types
KakaoCloud provides various instance types optimized for different use cases, allowing users to choose the most suitable instance for their workload and requirements. These instance types are designed to meet computing and storage resource needs.
Users can select a specific instance type when launching an instance, and costs are calculated proportionally based on the amount of resources used. This ensures efficient resource management and charges users only for what they actually use.
Available instance types on KakaoCloud include:
For detailed specifications and pricing of instance types, refer to the KakaoCloud official website.
Instance lifecycle
The instance lifecycle includes all stages from creation to termination. These stages are reflected by status values that indicate the current state of the instance, such as running, stopped, or deleted. By monitoring instance statuses, users can perform appropriate management tasks.
Understanding the full instance lifecycle—from provisioning to deletion—is essential for effective resource management.
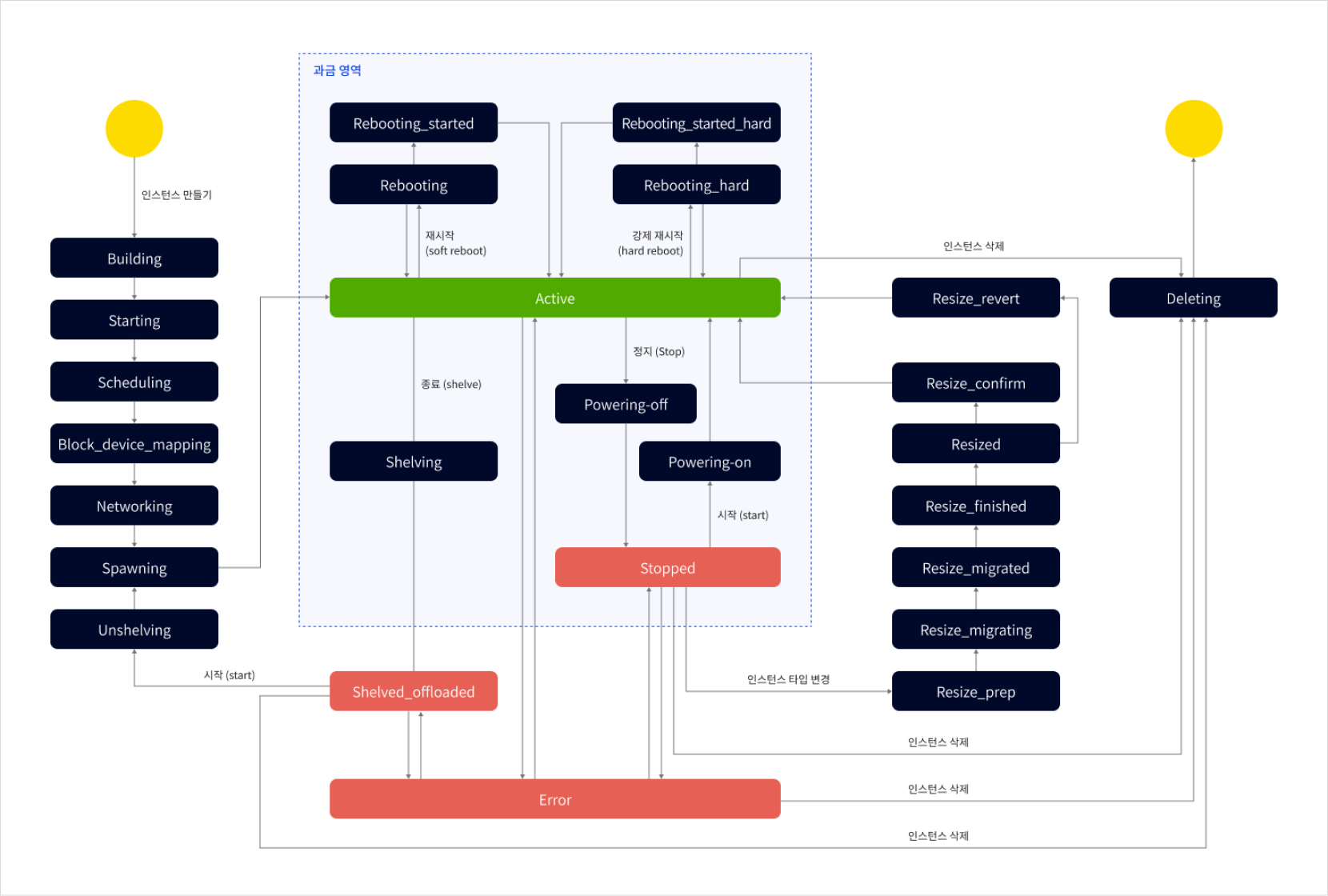 Instance lifecycle
Instance lifecycle
Commands/features
| Feature (CLI command) | Description | Resulting instance state |
|---|---|---|
Start (start) | Start the instance | Active |
Stop (stop) | Stop the instance | Stopped |
Shelve (shelve) | Shelve (terminate) the instance | Shelved_offloaded |
Soft reboot (soft reboot) | Restart the instance gracefully | Active |
Hard reboot (hard reboot) | Hard reboot the instance | Active |
Resize (resize) | Launch resize popup for instance type | - |
Delete/Terminate (delete or terminate) | Completely delete the instance | - |
Instance state and billing
The table below outlines billing status based on instance state.
| State | Description | Billed |
|---|---|---|
Active | Instance is running | Yes |
Shelved_offloaded | Instance terminated and resources released from hypervisor | No |
Stopped | Instance stopped but resources remain allocated | Yes |
Error | Instance is in error state | No |
Building, Starting, Scheduling, Block_device_mapping, Networking, Spawning | Provisioning in progress | No |
Rebooting, Reboot_started, Rebooting_hard, Rebooting_started_hard | Instance reboot in progress | Yes |
Shelving | Instance is being shelved | Yes |
Unshelving | Shelved instance is restarting | No |
Powering-off, Powering-on | Powering down or starting instance | Yes |
Resize_prep, Resize_migrating, Resize_migrated, Resize_finished, Resized, Resize_confirm, Resize_revert | Resize operations in progress | No |
Deleting | Instance is being deleted | No |
Configure instance
VMs are the core of cloud services, offering scalability and elasticity for dynamic workloads. Users can start, stop, or delete virtual servers (instances) based on business needs.
When launching a VM, users must first select an instance type, which determines computing resources. VM instances can scale up or out depending on requirements:
- Scale-up increases the resources (CPU, memory, etc.) of an existing instance to enhance performance.
- Scale-out adds more instances to distribute workloads, improving availability and scalability.
VM services also provide features for network configuration, making resources like instances, images, block storage, and security groups accessible on the network. Each instance is securely isolated.
A VM instance typically includes:
- Instance type: Defines the performance and size (CPU, memory, bandwidth, storage).
- Operating system: Supports various OSs, including Windows, Linux, and Unix.
- Storage type: Supports block, object, and file storage.
- Network: Connects to public or private networks, configurable via security groups, virtual networks, and IP settings.
Image
VM instances are launched using images, which contain the necessary OS and software configurations. Users can choose from a range of OS and application images based on their needs. Images follow the lifecycle of the instance and are billed accordingly.
Types of images:
| Image type | Description |
|---|---|
| Default | - Provided by KakaoCloud for Linux and Windows |
- Accessible to all users for quick, secure instance setup | | My image | - Custom images created by users within a project
- Can be used to launch new instances |
VM instances can be launched using KakaoCloud default images or user-created custom images.
Default images available
| Category | Image types |
|---|---|
| Linux | Ubuntu 20.04, 20.04 (GPU), 22.04, 22.04 (GPU), 24.04, |
| CentOS Stream 9, Rocky Linux 8.10, 9.4, | |
| Alma Linux 8.10, 9.4 | |
| Windows | Windows Server 2019, |
| Windows Server 2019 (+ MSSQL 2019), | |
| Windows Server 2022 |
Volume
VM instances use a root device volume containing the OS image to boot. This volume is provisioned via the Block Storage service during instance creation.
Volumes serve as the storage space for actual data. KakaoCloud currently supports SSD block storage only. Volumes can be created and attached to VM instances to store OS, file systems, or databases.
Volume states
Volume statuses can be viewed under Virtual Machine > Volume list.
| Volume state | Description |
|---|---|
Creating | Volume is being created |
Available | Volume is available |
In-use | Volume is attached to an instance (active, stopped) |
Reserved | Volume is attached to a shelved instance |
Attaching / Detaching | Volume is being attached/detached |
Extending | Volume is being resized |
Backing-Up | Snapshot of volume is being created |
Uploading | Volume is being saved as an image |
Deleting | Volume is being deleted |
Error | Volume is in an unusable error state |
Volume size limit
The volume size limit depends on the OS image. Each image defines a maximum volume size, so check this before configuring the volume.
| Item | Size (GB) |
|---|---|
| Minimum size | 1 |
| Maximum size | 16,384 |
Key pair
A key pair is used for secure access to VM instances. It consists of a public key and a private key. Users must manage key pairs carefully and store both keys securely.
Typically, the public key is registered on the cloud platform, and the private key is used during authentication. This enhances access control and security. Once registered, only that public key can be used. Key pairs can be specified when creating or connecting to an instance.
Private key loss may lead to loss of access to the instance. Ensure encryption, avoid sharing or duplicating keys, and safeguard them thoroughly.
Network and security
All VM instances are deployed within a VPC environment.
Virtual Private Cloud (VPC) allows users to configure private networks within the cloud, enabling fine-grained control and enhanced security for instances. Users can select VPC and subnets during instance creation and assign public IPs if necessary.
Public IP
A public IP allows a VM instance to communicate over the internet. Users can decide whether an instance should receive a public IP from the IP pool.
The IP remains attached until the instance is stopped or terminated. For persistent use, assign a static public IP to the instance or network interface. Public IPs incur ongoing charges and can be reassigned between instances via detach/attach operations.
IAM-based role management
Virtual Machine IAM (Identity and Access Management) supports role-based access control (RBAC) to manage users and groups. Roles define what actions a user can perform within a project.
All VM resources are created and managed under a project. Project-level users (Project Admin/Project Member) can perform tasks such as creation, modification, and deletion. However, only the key pair creator can delete their own keys.
By using IAM, access to instances can be controlled effectively, enhancing security and stability through appropriate permissions.
| IAM role | Project Admin | Project Member | Project Reader |
|---|---|---|---|
| Manage project members | ✓ | ||
| Set public IP config | ✓ | ||
| Manage instances | ✓ | ✓ | △ (view only) |
| Manage volumes | ✓ | ✓ | △ (view only) |
| Manage images | ✓ | ✓ | △ (view only) |
| Manage key pairs | ✓ | ✓ | △ (view only) |