Subnet
A Subnet is a subdivided network area within a VPC, allowing partial partitioning of IP addresses for segmentation. Each subnet represents a specific network area, enabling the VPC to be divided into multiple subnets for better management according to purpose and usage. In VPC, you can create resources such as BCS instances by specifying a subnet. It's important to note that subnets are constrained to a single Availability Zone (AZ), prohibiting the extension of a single subnet across multiple AZs.
Within the IP address range of a VPC, you can set IPv4 CIDR blocks. By configuring subnets across multiple AZs, you can deploy applications in a distributed manner. This ensures continuous availability of applications even in the event of a failure in a specific AZ.
Subnet diagram
The following diagram shows two VPCs in one region. Each VPC has public and private subnets and an internet gateway.
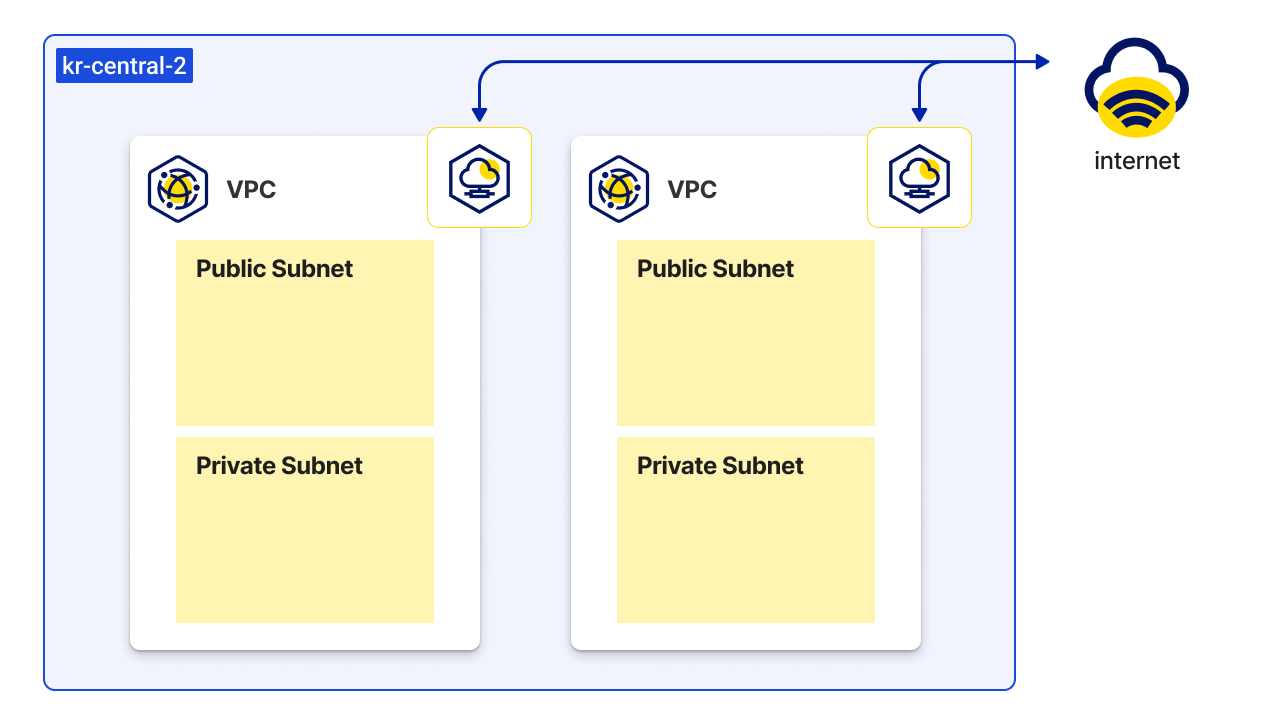 Subnet Diagram (based on kr-central-2)
Subnet Diagram (based on kr-central-2)
Subnet types
Subnets can be configured as a public subnet or a private subnet based on its routing configuration.
-
Public subnet: Refers to a subnet with a route to an internet gateway configured in the associated route table. This route allows resources in the public subnet to access the internet.
-
Private subnet: Refers to a subnet without a route to an internet gateway configured in the associated route table. Resources in a private subnet require a NAT Instance to access the public internet.
When creating a subnet, specify the IP addresses based on the VPC configuration.
- Resources in the subnet must communicate via IPv4.
- Regardless of the subnet type, the IPv4 address range of a subnet is always private IP.
Subnet IP CIDR blocks
When an instance is deployed in a specific subnet, one IP from the IP address range is randomly assigned. The IP address range of a subnet can be specified using Classless Inter-Domain Routing (CIDR) notation. Multiple subnets can be configured within a single VPC, and the allowable CIDR block size for each subnet ranges from a /20 netmask to a /26 netmask. When creating multiple subnets within a VPC, ensure that the CIDR blocks of the subnets do not overlap.
For example, in a VPC with a CIDR block of 10.0.0.0/16, you can create subnets and divide this CIDR block into two subnets, each supporting 4,096 IP addresses, as follows.
- VPC CIDR Block: 10.0.0.0/16
- Subnet #1: 10.0.0.0/20 CIDR Block (addresses between 10.0.0.0 and 10.0.15.255)
- Subnet #2: 10.0.16.0/20 CIDR Block (addresses between 10.0.16.0 and 10.0.31.255)
Effective VPC utilization relies on well-designed subnet CIDR blocks. To calculate and create IPv4 subnet CIDR blocks, you can search for tools like "subnet calculator" or "CIDR calculator" on the internet. These tools help you compute and generate the necessary CIDR blocks tailored to your requirements.
Reserved IP Addresses
In the CIDR block of a subnet, the first 6 IP addresses and the last IP address, a total of 7 addresses, are reserved and cannot be assigned to resources such as BCS instances. For example, if the CIDR block of the subnet is 10.0.0.0/24, the reserved IP addresses are as follows:
| IP Address | Description |
|---|---|
| 10.0.0.0 | Network address |
| 10.0.0.1 | Reserved by KakaoCloud for the default gateway |
| 10.0.0.2 | Reserved by KakaoCloud for future use |
| 10.0.0.3 | Reserved by KakaoCloud for future use |
| 10.0.0.4 | Reserved by KakaoCloud for DHCP usage |
| 10.0.0.5 | Reserved by KakaoCloud for DHCP usage |
| 10.0.0.255 | Network broadcast address |
Example of reserved IP addresses
Associate subnet with route table
Each subnet must be associated with a route table that specifies the allowed route for Outbound traffic leaving the subnet. Upon creation, each subnet is automatically associated with the Main route table of VPC. All subnets can change the associated route table. Refer to the Route Table document for more details.
Delete subnet
If a subnet is no longer needed, it can be deleted. However, the subnet containing the network interface cannot be deleted. This means that you must delete all instances of the subnet (including the Load Balancer) before you can delete the subnet.