Components
Each component of KakaoCloud IAM has a distinct role and forms the foundation for systematically managing resources and permissions across KakaoCloud.
IAM consists of the following key components:
Organization
An organization is the top-level unit in the KakaoCloud IAM hierarchy.
A single organization can include multiple projects, users, groups, and service accounts.
It enables centralized management of login settings, user invitations, and group/project creation.
- At the organization level, you can control access to global services such as Billing, Cloud Trail, and Alert Center.
- A single user account can belong to multiple organizations but must be unique within each organization.
- Examples of organization-level roles:
Organization Admin, Organization Leader, IAM Organization Admin, IAM Organization Viewer, Billing Admin, and service-specific organization roles (e.g., Alert Center Organization Manager).
For available organization roles and their permission scopes, see Organization roles.
For details on organization creation, login, and security settings, refer to Create and manage organization.
Project
A project is the fundamental unit where cloud resources are created and operated.
Resources such as virtual machines (VMs), networks, storage, and data analytics services are all managed within projects, and most IAM permissions operate at this level.
- Resource quotas, access permissions, and service account settings are managed per project.
- Notification policies, monitoring configurations, and Cloud Trail integrations can also be managed per project.
- Examples of project-level roles:
Project Admin, Project Member, IAM Project Admin, IAM Project Viewer, and service-specific roles (e.g., Pub/Sub Publisher).
For available project roles and their permission scopes, see Project roles.
For details on creating, updating, or deleting projects, see Create and manage project.
User
A user is an individual account that logs in to the KakaoCloud console or makes API calls.
Users are email-based and must belong to an organization or project to receive permissions.
- A user can belong to multiple organizations and projects, each with different IAM roles.
- Roles can be assigned directly to a user or inherited through group membership.
- Login history and API call activity are auditable via Cloud Trail.
- Roles should be granted based on the Principle of Least Privilege.
See Manage users to learn how to register and manage users at the organization level.
Group
A group is a collection of users used to manage IAM roles efficiently in bulk.
When a role is assigned to a group, it automatically applies to all its members.
If a user is removed from the group, the permissions granted through that group are revoked accordingly.
This structure simplifies permission management and enhances auditability for security operations.
| Policy type | Description |
|---|---|
| Nesting | Other groups cannot be included within a group. |
| Eligible members | - Only users can be added (service accounts excluded). - A user can belong to multiple groups simultaneously. |
| Role assignment and retention | - Supports IAM, organization, project, and service-specific roles. - When a group is deleted, roles granted through it are revoked, but directly assigned roles remain. |
| API token handling | Tokens issued through a group are immediately invalidated when a user is removed. |
Example: Using groups to efficiently manage organization- and project-level permissions in KakaoCloud IAM.
Multiple IAM groups can exist within an organization, each managing users and roles according to operational purposes.
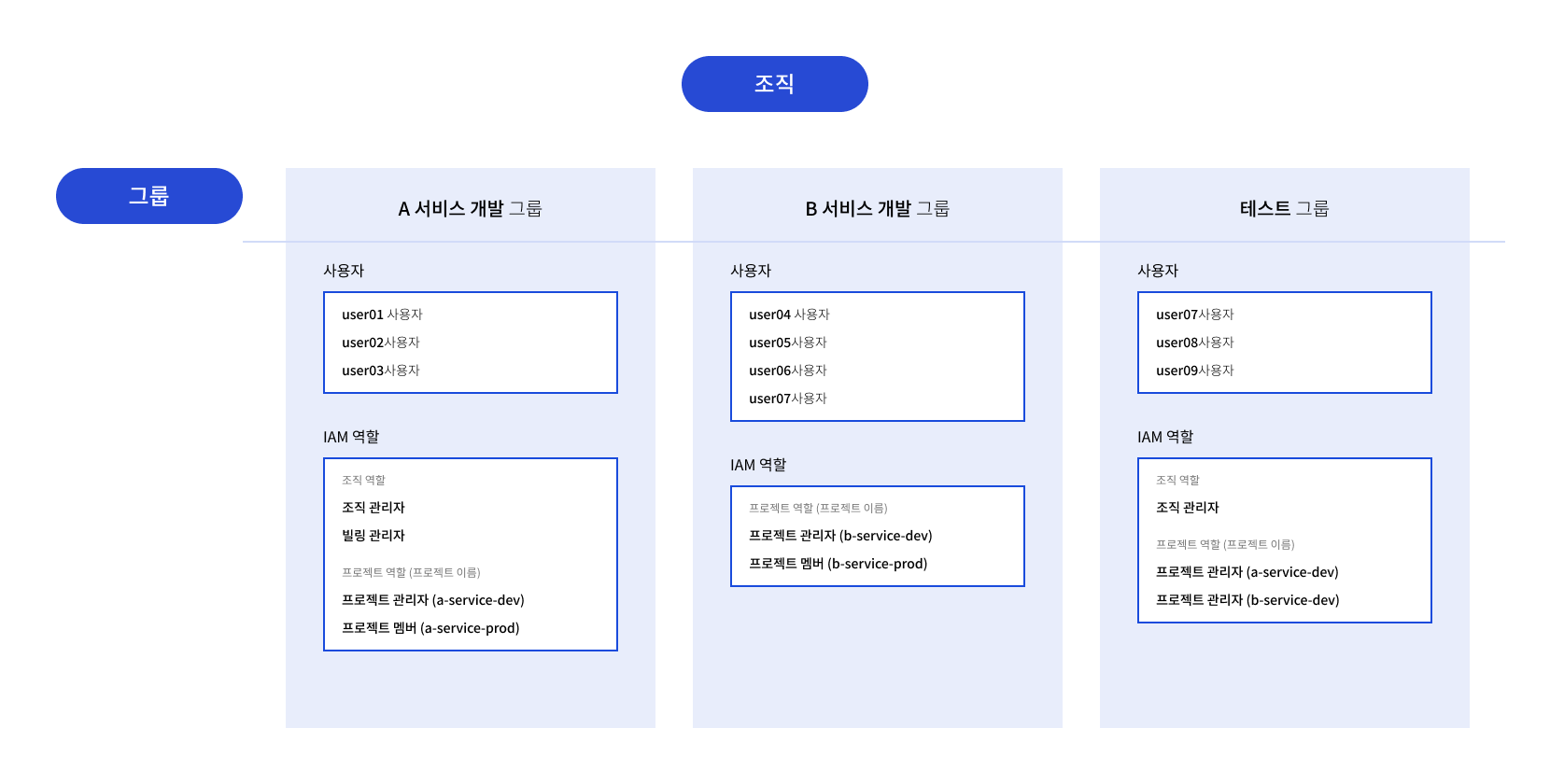 Group structure
Group structure
See [Create and manage groups]/start/console-guide/credentials) for more details on group configuration and permission management.
Service account
A service account is a non-interactive account created by users to access KakaoCloud APIs without console login.
It is mainly used for automated tasks such as CI/CD pipelines or system integrations, with access controlled by project-level IAM roles.
| Policy type | Description |
|---|---|
| Account format | {custom-name}-{project-name}@kc.serviceaccount.com |
| Login method | Not available (API only) |
| Authentication method | Uses IAM or S3 access keys for token issuance. See Get credentials for a service account for details. |
| Credential limits | Up to 2 IAM access keys and 2 S3 access keys per account. |
| Account limit | Up to 100 service accounts per project, including inactive ones. |
| Role assignment | Only project-level roles can be assigned (organization roles not supported). Some API operations may require explicit role assignment within the project. |
Service accounts are not listed under IAM users and do not affect IAM user quotas.
See Create and manage service accounts to learn how to create and manage service accounts.
Service agent account
A service agent account is a system-managed account automatically created by KakaoCloud services.
It is used internally by KakaoCloud to perform backend operations such as resource creation, scaling, or linking—without user intervention.
For example, when you add a node pool in Kubernetes Engine, a service-specific agent automatically creates the corresponding Virtual Machine instances.
| Policy type | Description |
|---|---|
| Account format | {project-name}@{service-name}.kc.serviceaccount.com |
| Modification/deletion | Cannot be created, modified, or deleted manually. All service agent accounts in a project are deleted when the project is deleted. |
| Role and permission conditions | Automatically assigned the minimal IAM roles required for service operations. Internal-only accounts — cannot log in to the console or make API calls directly. |
See View service agent for how to check service agent accounts in the console.