Integrate KakaoCloud with Microsoft Entra ID as IdP
Microsoft Entra ID (formerly Azure AD) is an external identity provider provided by Microsoft that allows you to log in to KakaoCloud with a Microsoft account.
This tutorial guides you through how to manage your KakaoCloud organization by linking your IdP with Microsoft Entra ID.
- Estimated time: 40 minutes
- Pre-requisites
- KakaoCloud as an Org Owner, create an organization
- Create a Microsoft Entra ID tenant and register users
- User accounts registered in the Microsoft Entra ID tenant
After setting up the login account as an IdP, you cannot change it back to KakaoCloud.
IdP integration
- This course is conducted using the OAuth linkage method.
- You can check the SAML integration method in Service > IdP SAML Integration tab.
Step 1. Issue integration information from Microsoft Entra ID
-
After logging in to the Microsoft Azure Portal, select the menu icon in the upper left corner and select the Microsoft Entra ID menu.
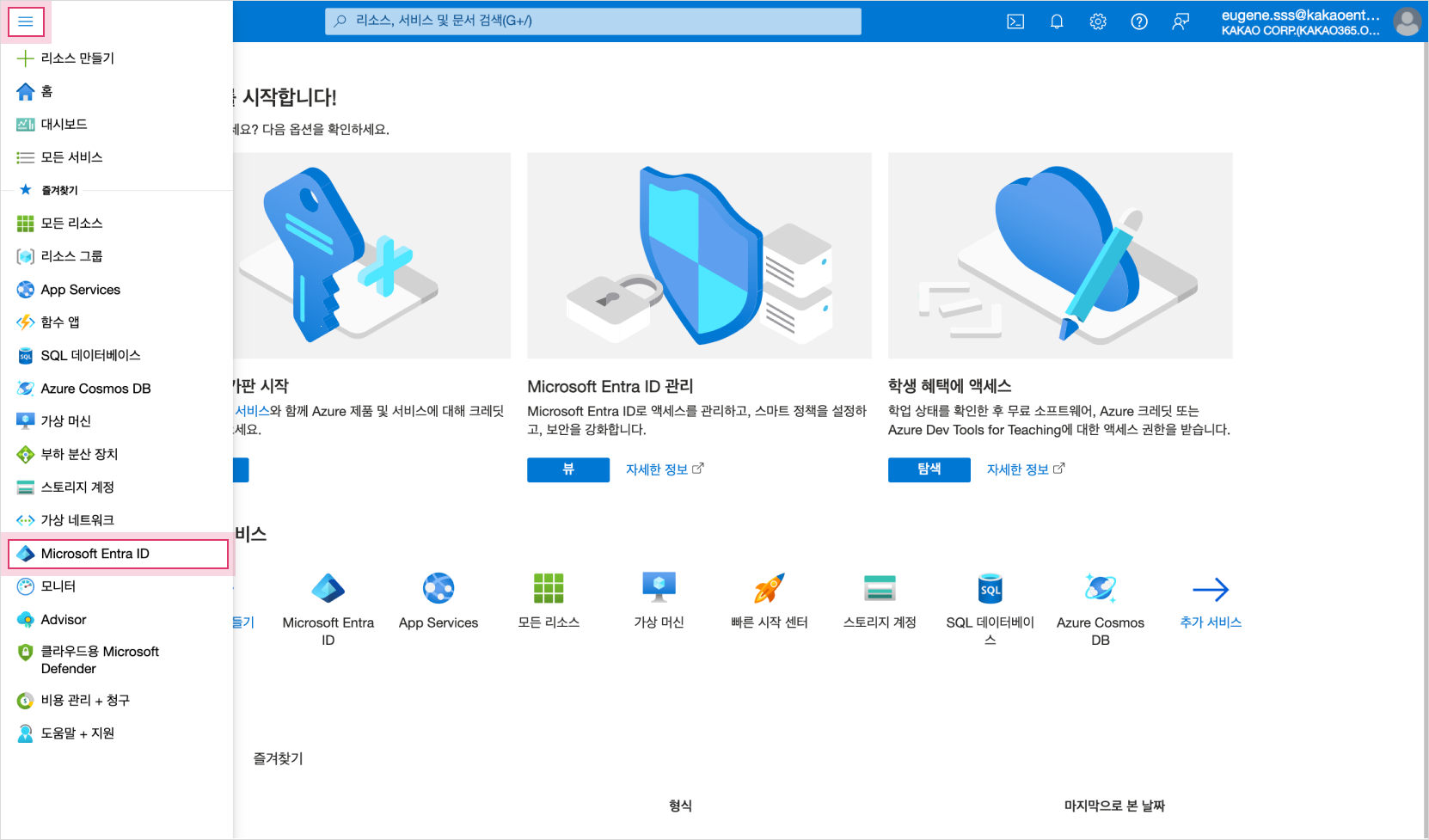 Microsoft Entral ID
Microsoft Entral ID -
Select the Management > App Registration menu on the left sidebar of Microsoft Entral ID, and select New Registration to register KakaoCloud as an app.
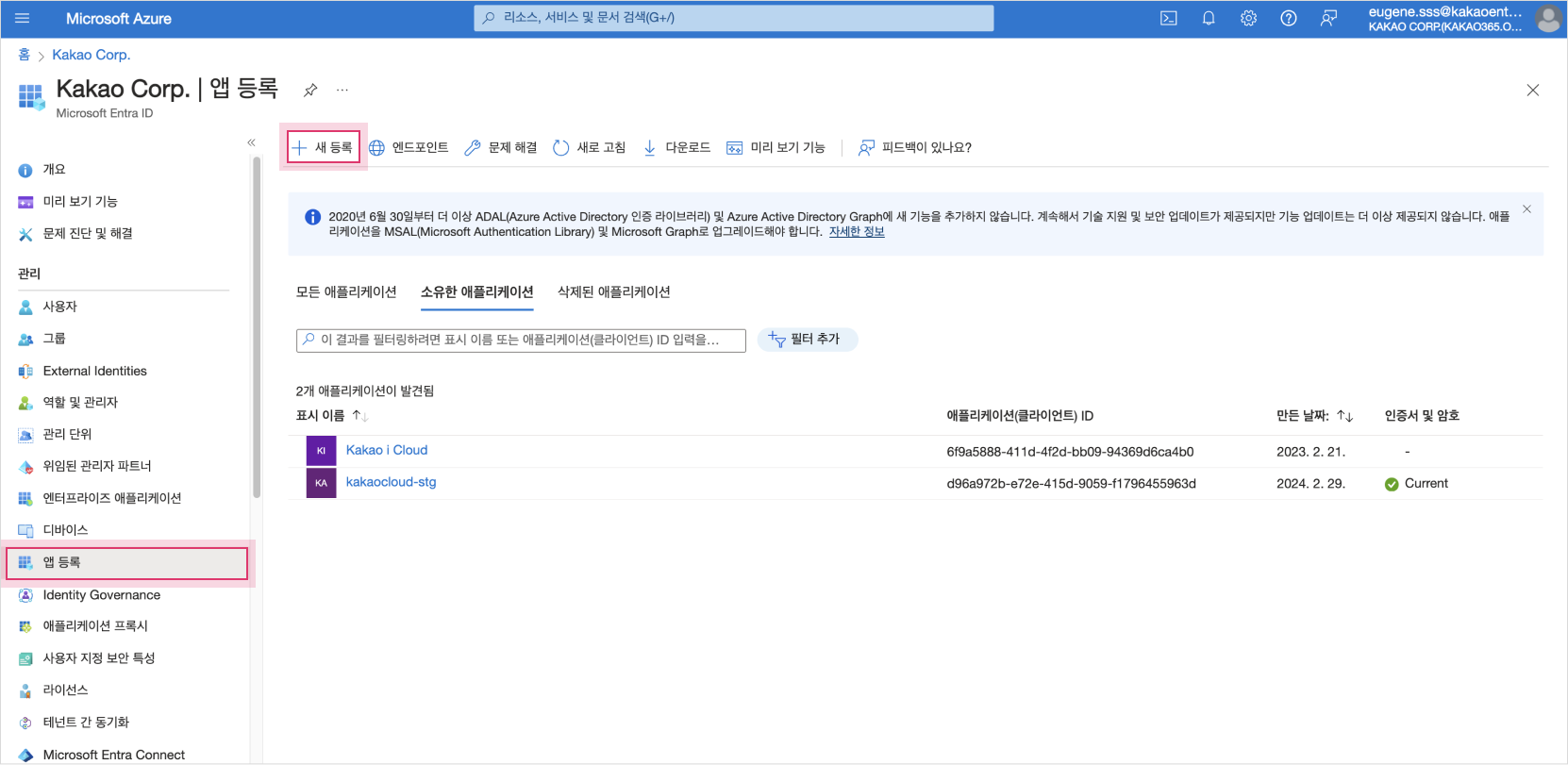 App Registration > New Registration
App Registration > New Registration -
In Application Registration, authenticate the user and register information so that the authentication response is returned to this URI.
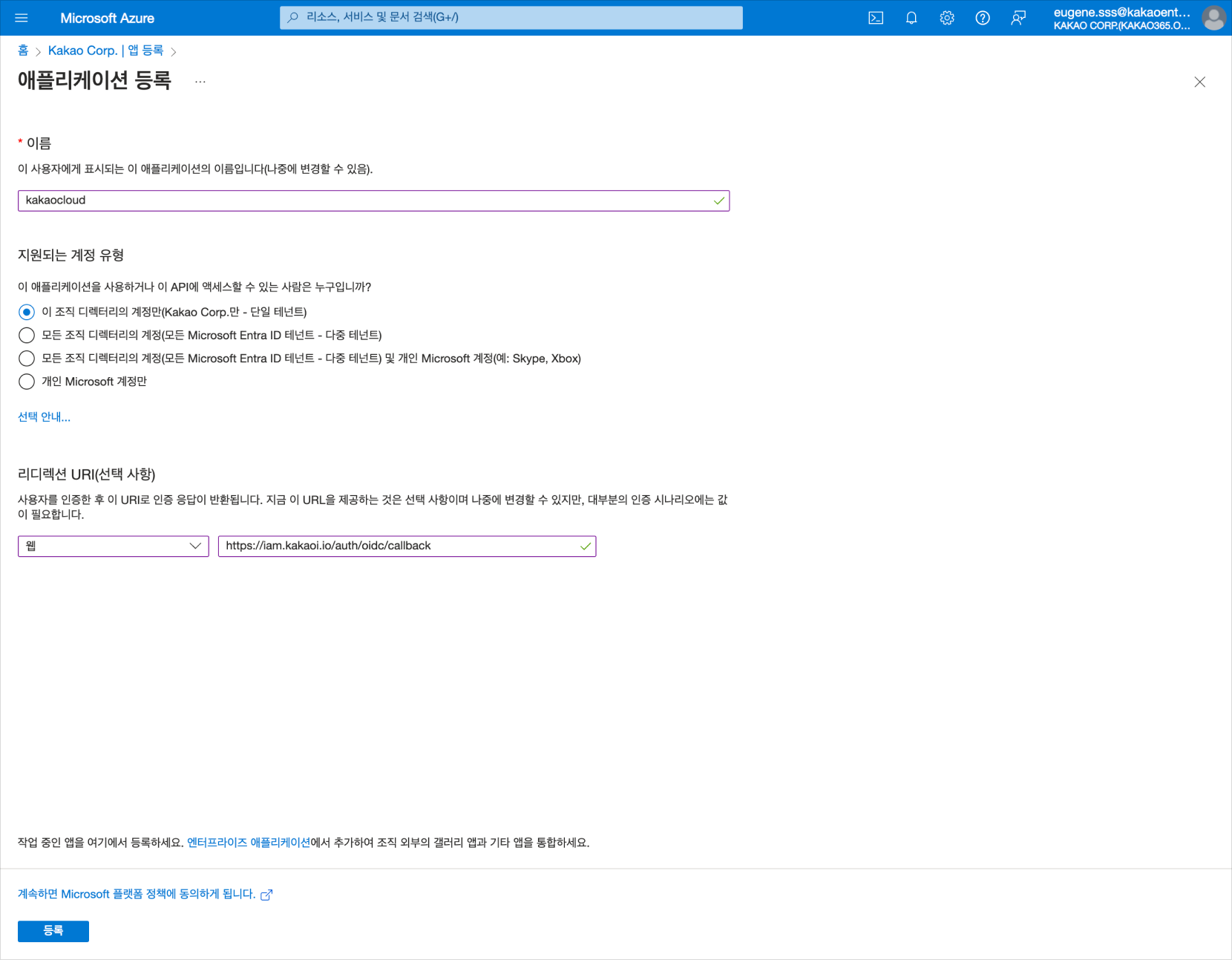 Application Registration
Application RegistrationCategory Description Name Enter kakaocloud(name to be displayed as an application)Supported account types Since you need to set login to only certain tenants, select Only accounts in this organization directory Redirect URI (optional) Type: Select Web
Redirect URI: Enter a fixed URI,https://iam.kakaocloud.com/auth/oidc/callback -
In Basic Information, copy the Application (client) ID, which is the
Client IDinformation, to the clipboard, etc.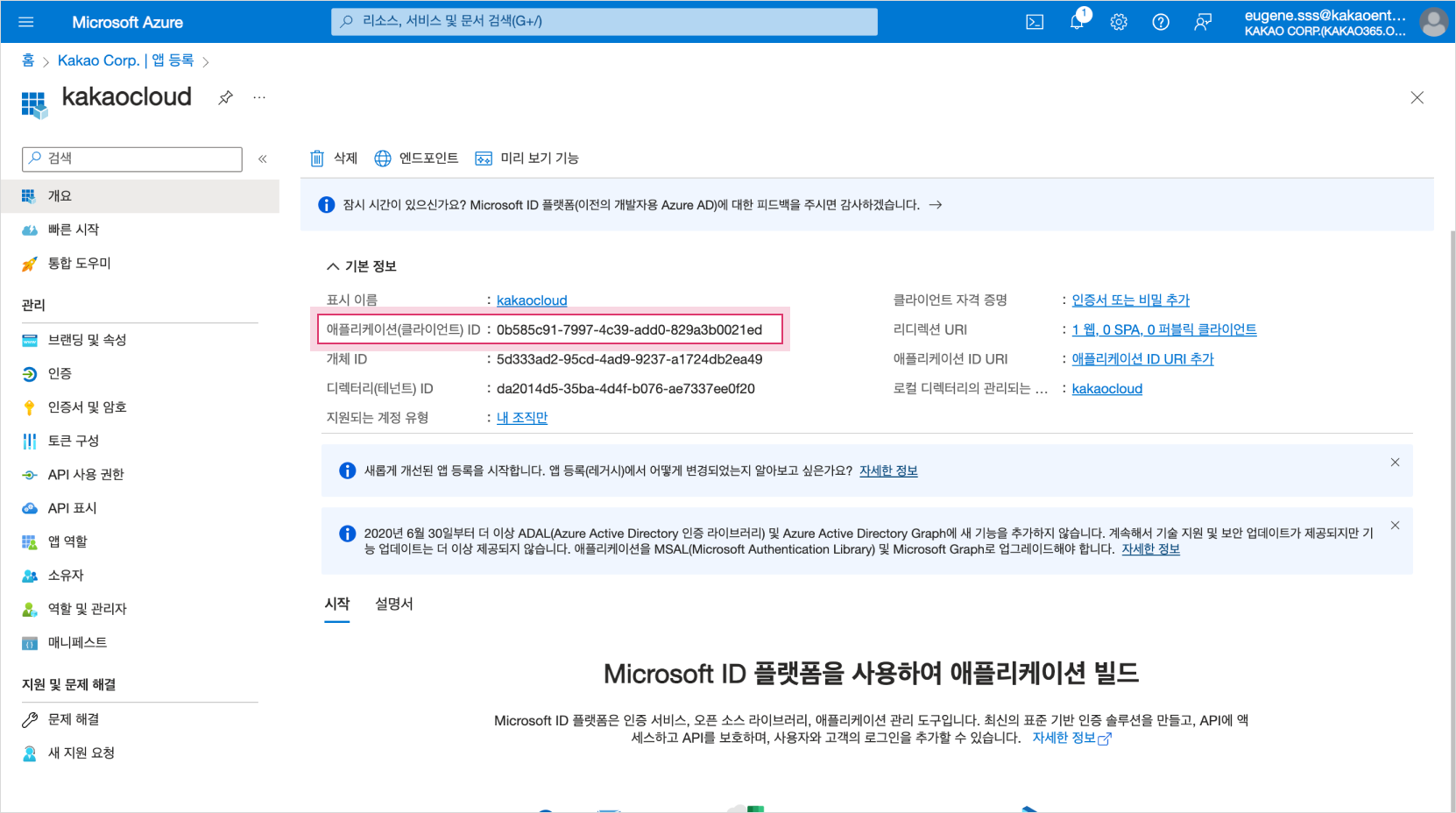 Registered application basic information
Registered application basic information -
Select Endpoint, then copy the OAuth 2.0 Authorization Endpoint (v2) and OAuth 2.0 Token Endpoint (v2) information to the clipboard, etc.
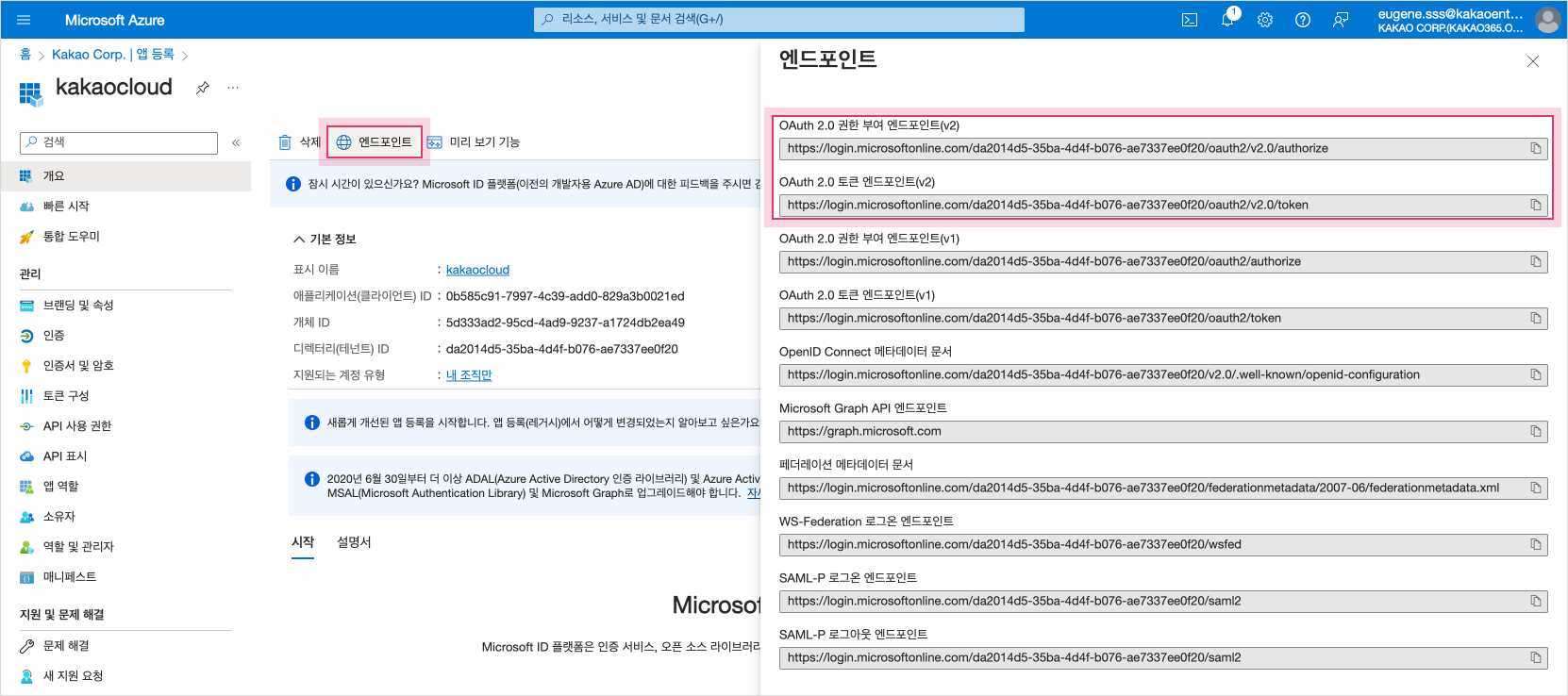 Copy Endpoint Information
Copy Endpoint InformationEndpoint Information Description OAuth 2.0 Authorization Endpoint (v2) Information entered in the Authorization URL field when registering a credential provider OAuth 2.0 Token Endpoint (v2) Information entered in the Token URL field when registering a credential provider -
Select Add Certificate or Secret to create a
Client Secret.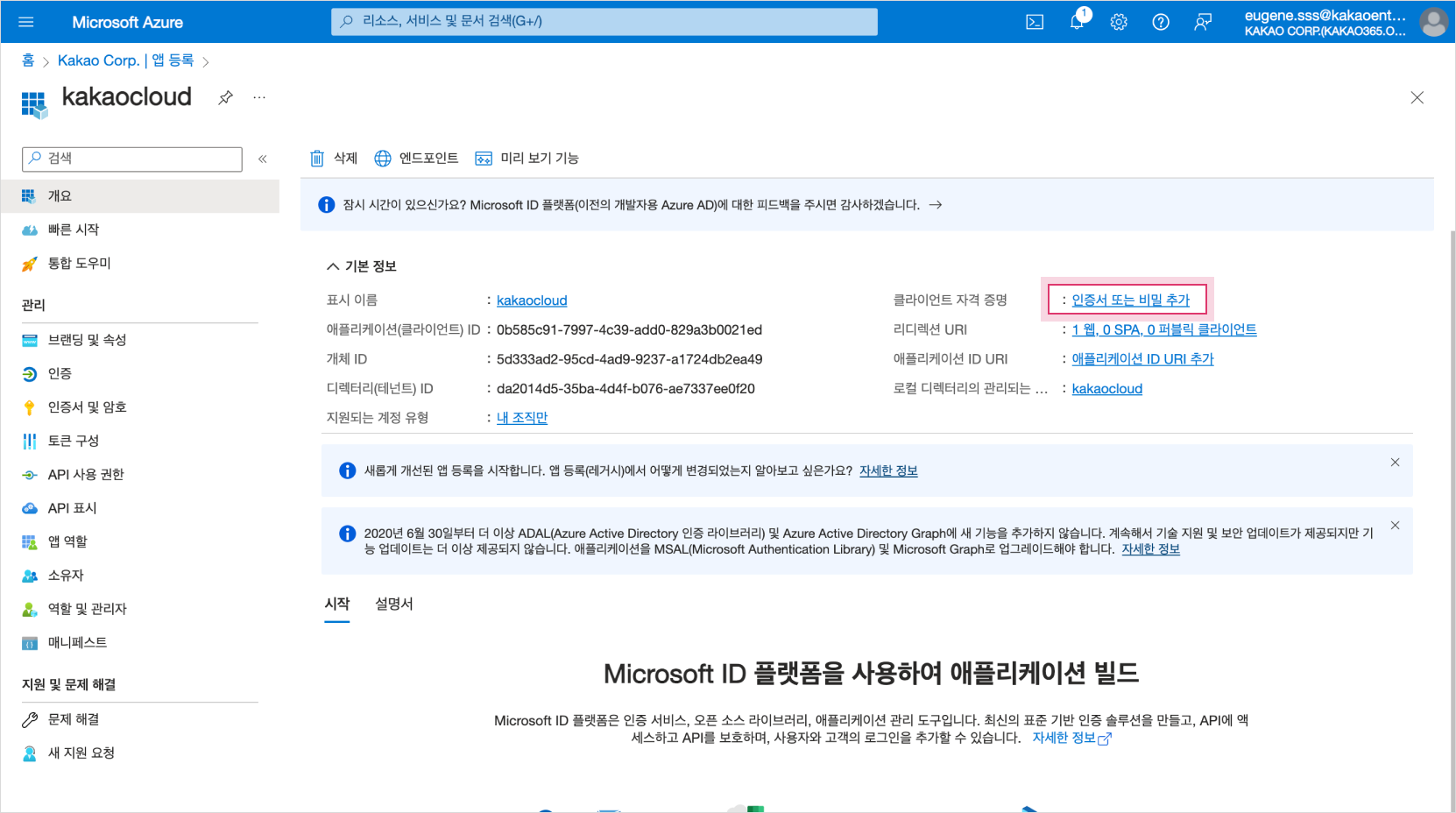 Add a certificate or secret
Add a certificate or secret -
Select New client secret to add a client secret.
When adding a client secret, you can only log in to the KakaoCloud console within the set expiration time.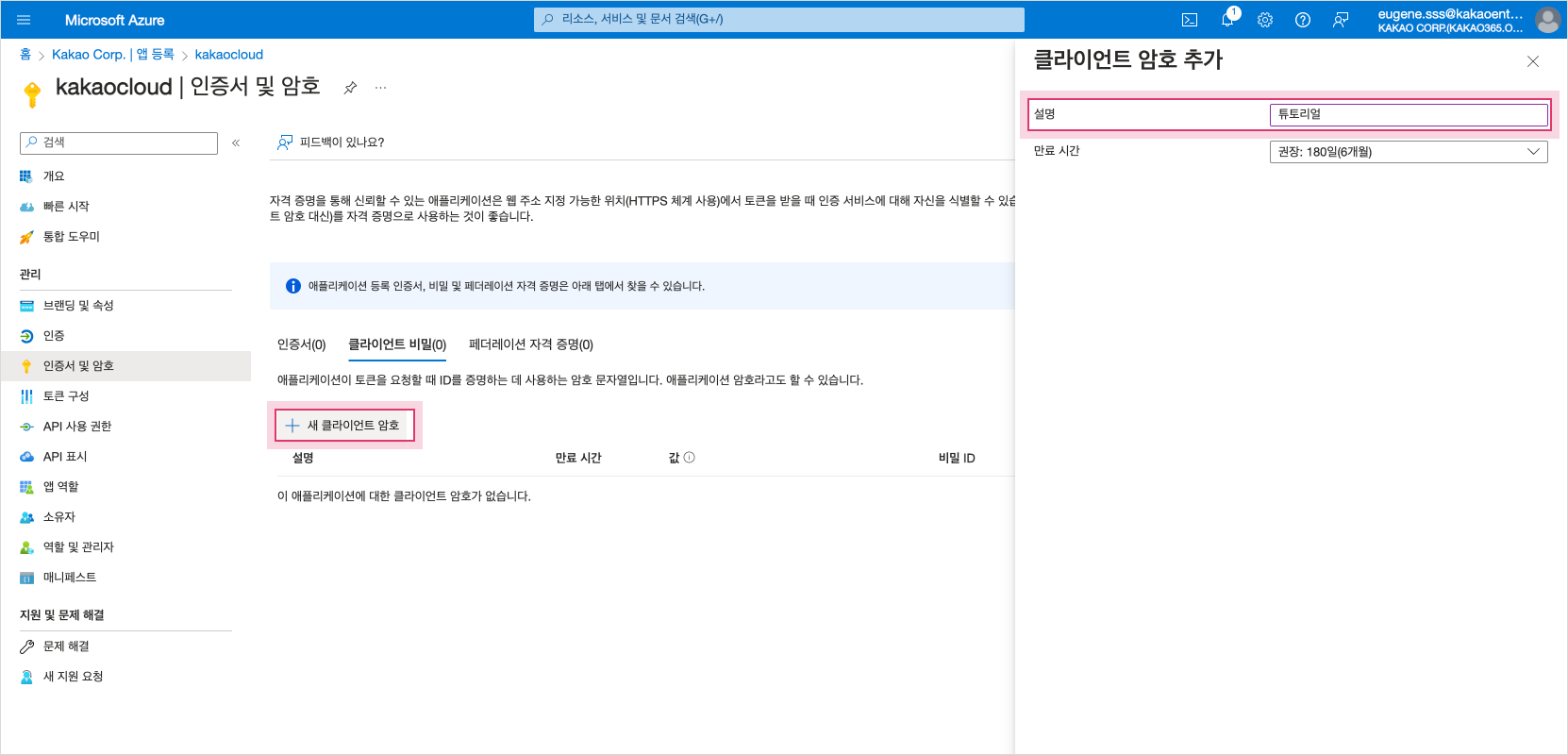 Add client secret
Add client secret -
Copy the newly created client secret value, which is the
Client Secretinformation, to the clipboard, etc. If you leave the screen, you will not be able to check theClient Secretinformation, so be sure to copy the information to the clipboard.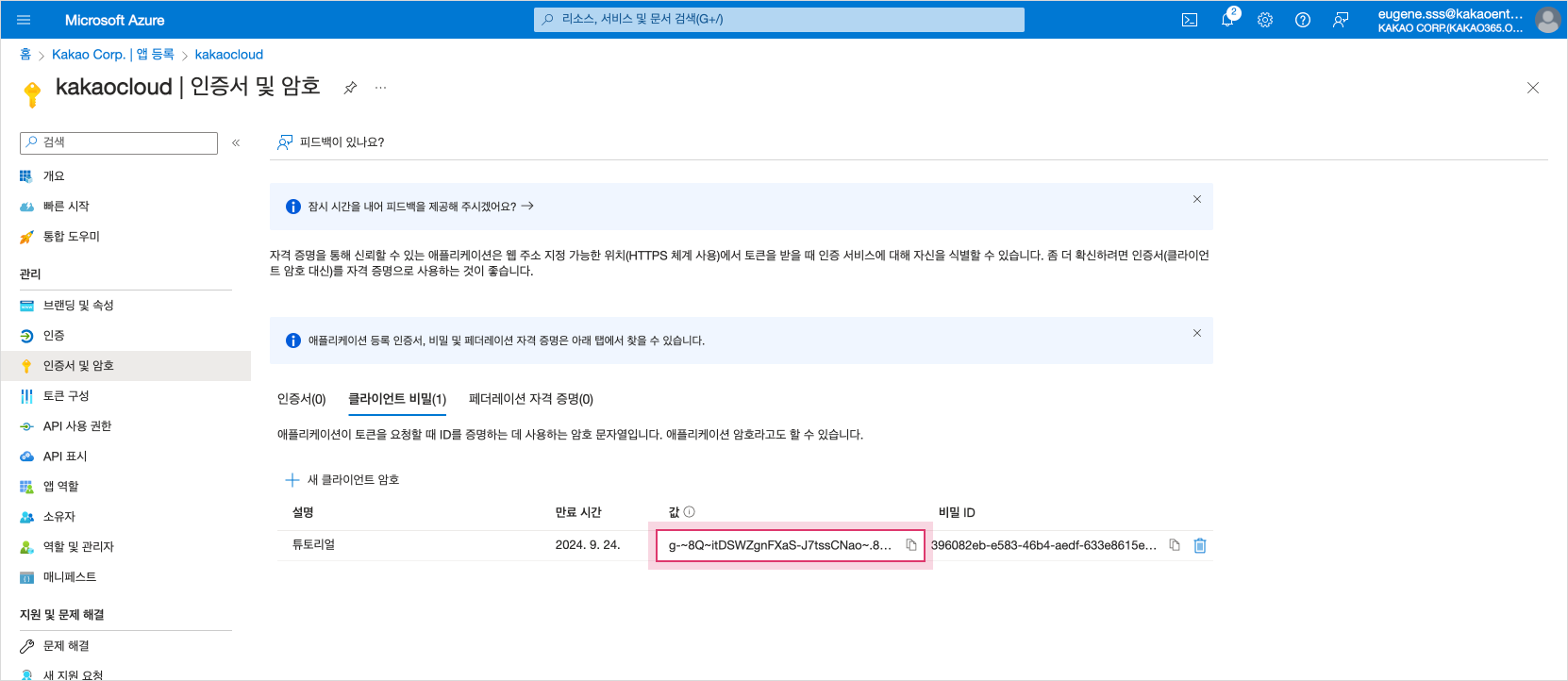 Copy client secret value
Copy client secret value -
After completing the above task, you can obtain a total of 4 pieces of information:
Client ID,Client Secret,Authorization URL, andToken URL.
Please use this information when registering IdP in the login settings.
Step 2. IdP registration
After obtaining the linkage information in Step 1, access the KakaoCloud console and register the IdP.
- Only the Org Owner can link the IdP.
-
Enter the organization name in the KakaoCloud console and log in with the Org Owner account.
-
Select the Organization Management Icon > Organization Management menu.
-
Select the [Login Settings] button.
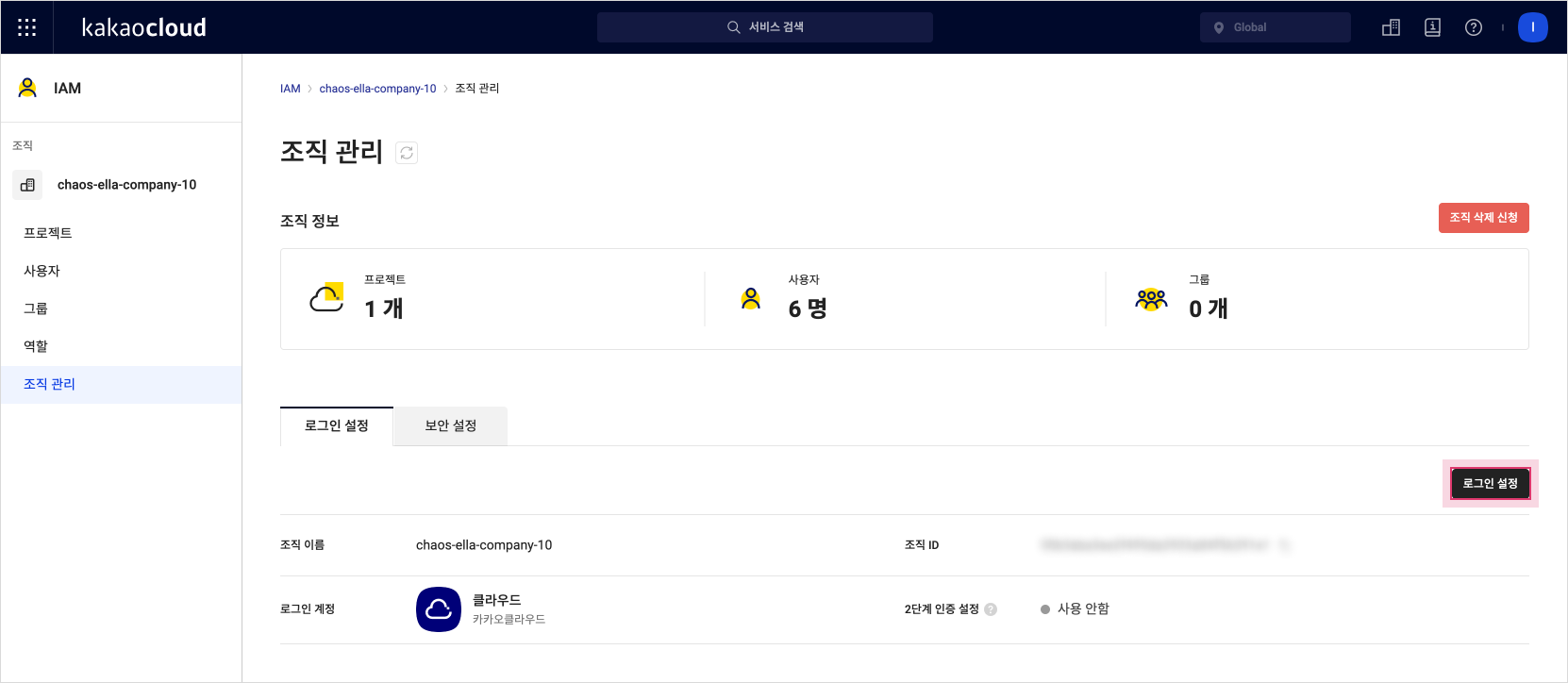 Login settings
Login settings -
Check the organization information on the login settings details page, select IdP Account, and then check the IdP linkage information from Step 1 and enter the linkage protocol and linkage information below.
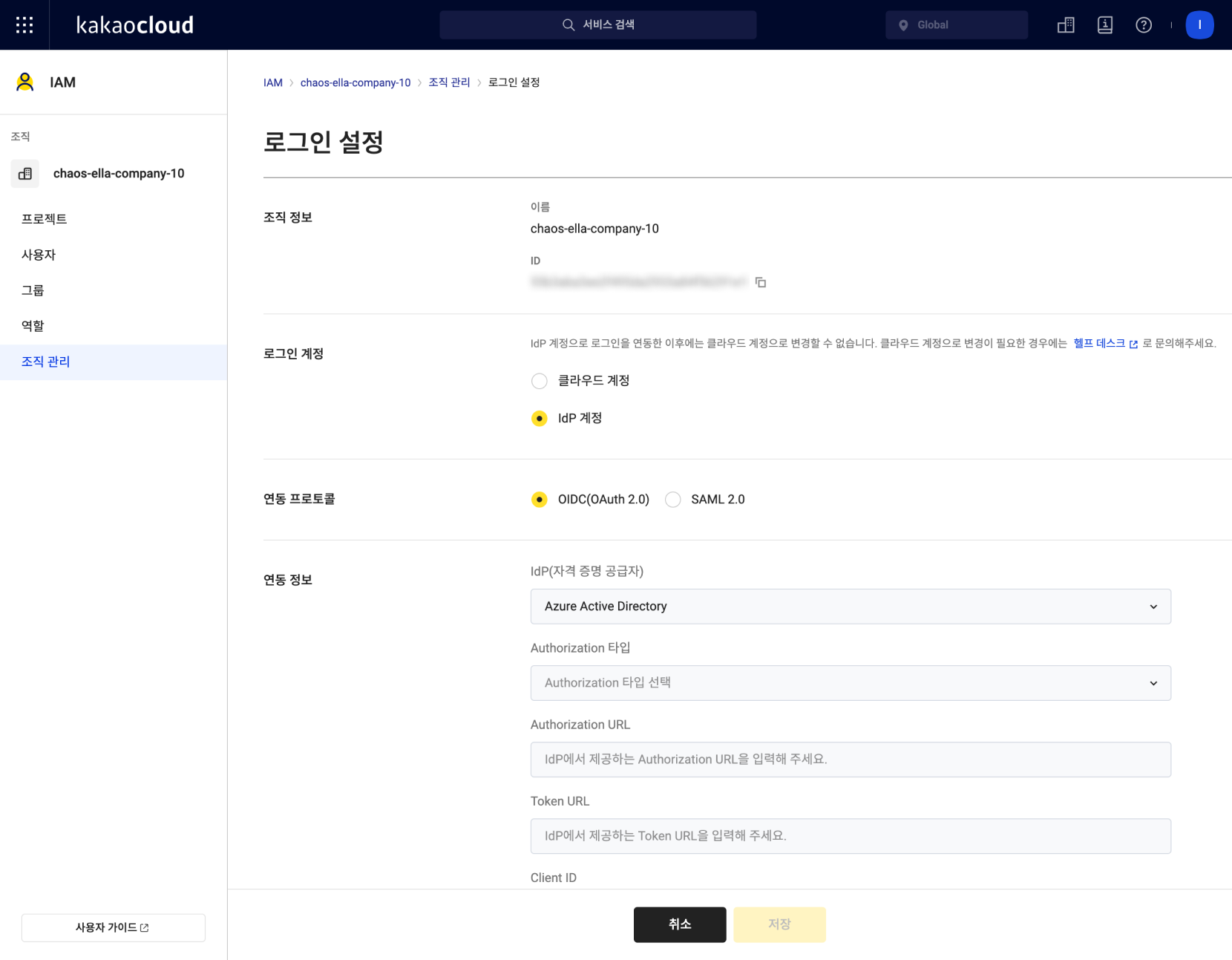 Enter linkage information
Enter linkage informationItem Category Description Integration Protocol Select OIDC (OAuth 2.0) Integration Information IdP (Identity Provider) Select Azure Active Directory Authorization Integration Type Select POST body Authorization URL Enter information obtained from the OAuth 2.0 authorization endpoint (v2) Token URL Enter information obtained from the OAuth 2.0 token endpoint (v2) Client ID Enter information obtained from the application (client) ID Client Secret Enter information obtained from the value string of the client secret -
Select Test Integration to proceed with the IdP integration test. Enter the ID and password on the login screen of the external identity provider, and the test is completed if the integration is successful.
Step 3. Log in to KakaoCloud console
Change the existing account used to log in to the KakaoCloud console to the External Credential Provider Account Linked to IdP.
-
After accessing the KakaoCloud console, log out of the KakaoCloud account you previously logged in to.
-
Enter the organization name in KakaoCloud > Console Login and select the [Next] button.
-
Microsoft Azure Login > Select Account, log in with the Microsoft Entra ID account linked to the IdP.
-
You can confirm that you are logged in with an external credential provider account.
Register and manage users in your organization
- All users in the Microsoft Entra ID tenant will not be automatically added as users in your KakaoCloud organization just by setting up the IdP linkage.
- Therefore, users will be added only after the first login to the KakaoCloud console with the Microsoft Entra ID account.
- If the email address of a user already registered in your KakaoCloud organization is the same as the Microsoft Entra ID email address, you will be logged in as a registered IAM user.
Step 1. Register users in your KakaoCloud organization by logging in with IdP account
The process of automatically registering users in your KakaoCloud organization by logging in to the KakaoCloud console with a Microsoft Entra ID account is as follows.
If you are not a user within the Microsoft Entra ID tenant (ex. new employee), registering a user within the tenant must be done first to log in to the KakaoCloud console.
-
Log in to the KakaoCloud console with one account among the Microsoft Entra ID tenant users.
-
Log out again and log in with the Org Owner account.
-
Select the Organization Management icon > User menu.
-
You can confirm that the user logged in in step 1 is registered within the KakaoCloud organization.
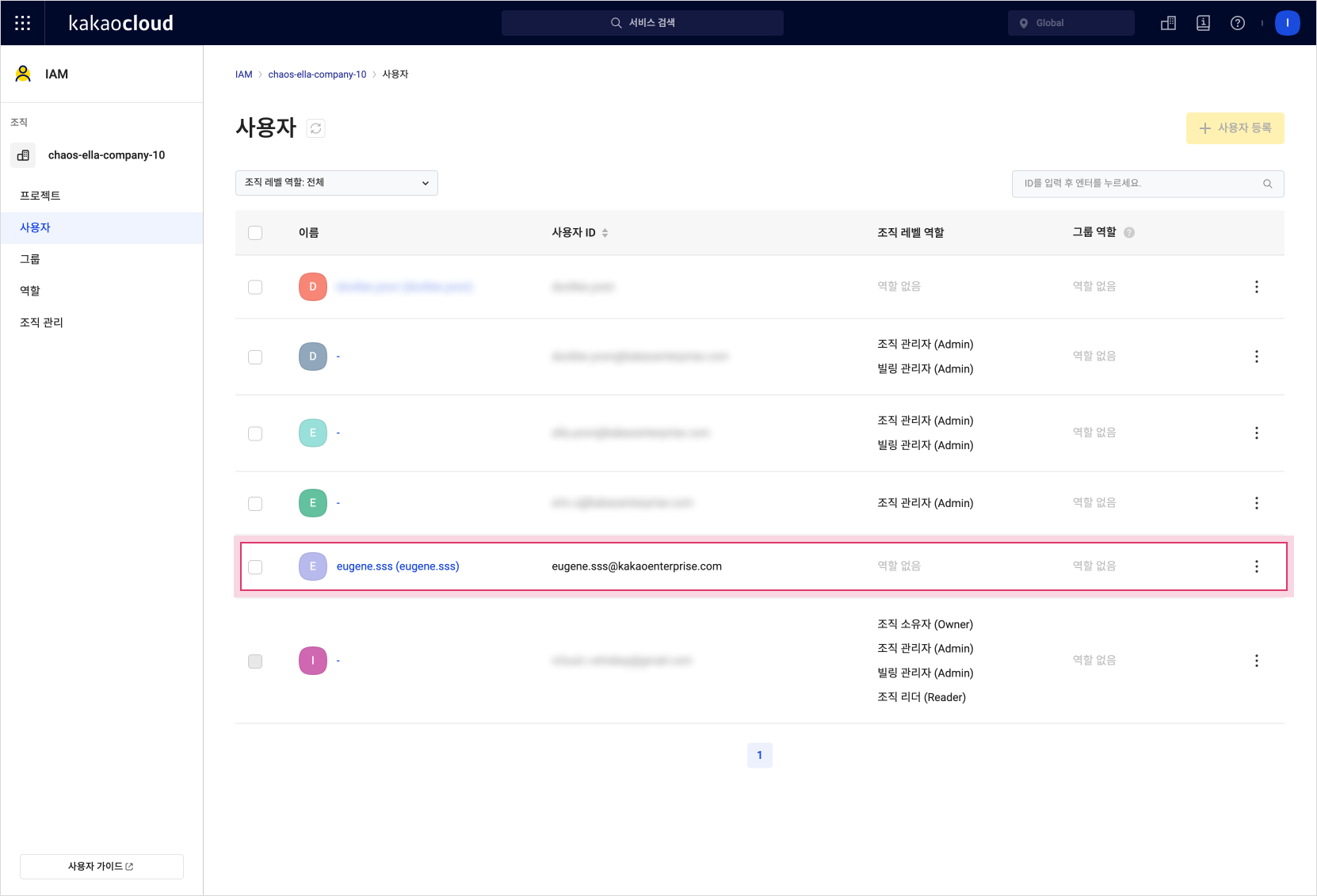 Check registered users
Check registered users
Step 2. Grant and delete organization roles to users
If the email address of a user already registered within the KakaoCloud organization is the same as the Microsoft Entra ID email address, the user will log in as a registered IAM user.
Therefore, the roles and permissions granted to the user will be maintained.
The process of granting and deleting organization roles (organization leaders) to the user registered above is as follows.
Grant roles
-
Log in to the KakaoCloud console with the Org Owner (Owner) account.
-
Select the Organization Management icon > User menu.
-
Select Add organization role from the More icon of the registered user.
-
In the organization role Settings, select Organization Reader, the role to be granted.
-
The Organization Reader role is granted.
Delete role
-
Log in to the KakaoCloud console with the Org Owner account.
-
Select the Organization Management icon > User menu.
-
Select Delete organization role from the More icon of the registered user.
-
In the organization role Settings, check the Organization Reader role to be deleted, and then select the Next button.
-
After checking the role to delete, Organization Reader, select the Delete button to complete the role deletion.
Delete User in Organization
If you need to delete a user completely within the organization (ex. a former employee), you can delete the user through the following process.
- If you delete a user only in the KakaoCloud console, the user will be registered as a user again when logging in with an external credential provider account.
- If you delete a user only in the Microsoft Entra ID tenant, the user will not be deleted within the KakaoCloud organization.
- Therefore, both the
Microsoft Entra IDtenant and theKakaoCloud consolemust be deleted.
Step 1. Delete user within the Microsoft Entra ID tenant
-
Log in to the Microsoft Azure Portal with an account that has user administrator rights, and then select the Microsoft Entra ID menu.
 Microsoft Entra ID
Microsoft Entra ID -
Select the Member menu, then search for and check the user you want to delete.
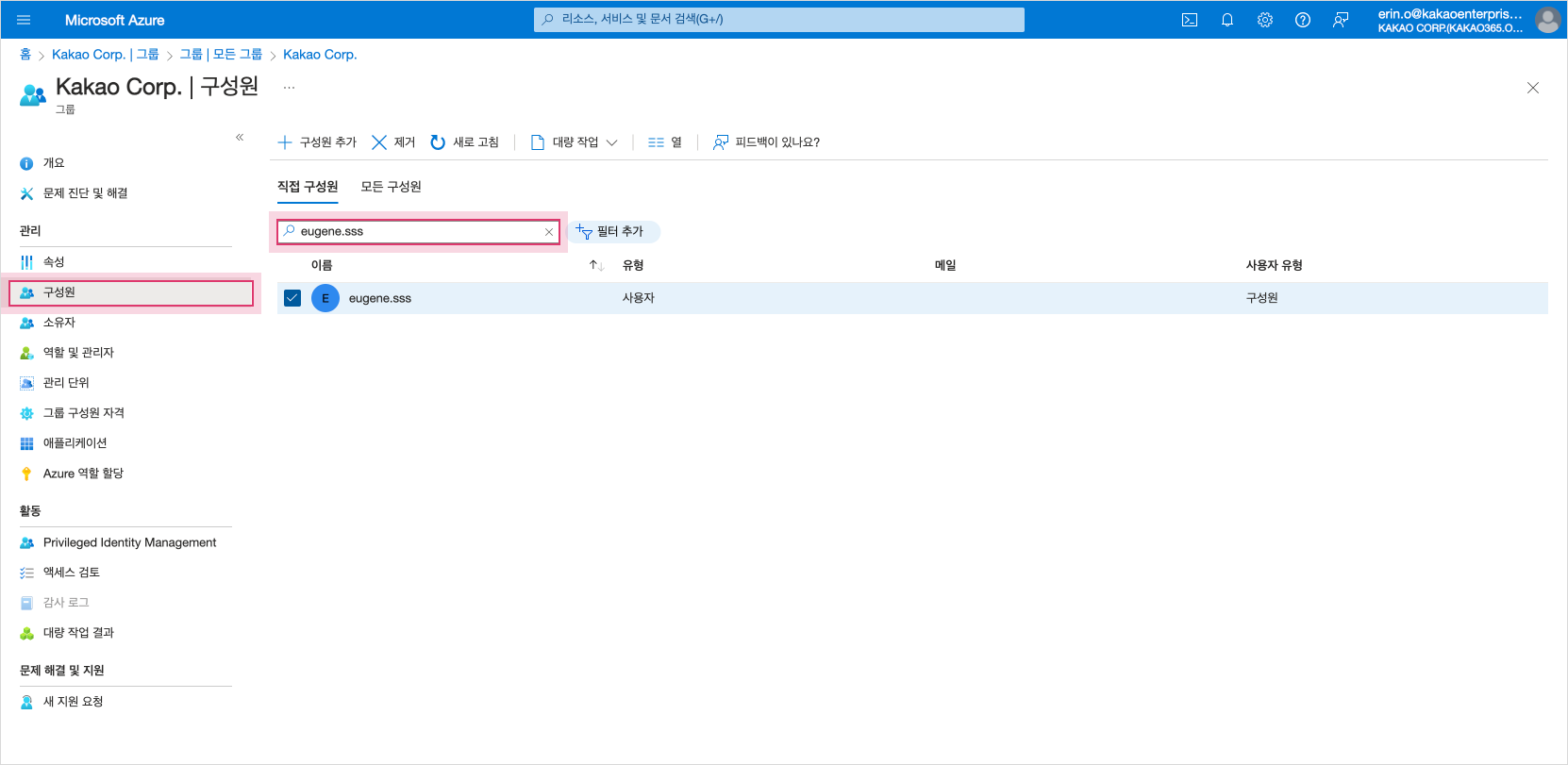 Check the user to delete
Check the user to delete -
Select the Remove button at the top to remove the user.
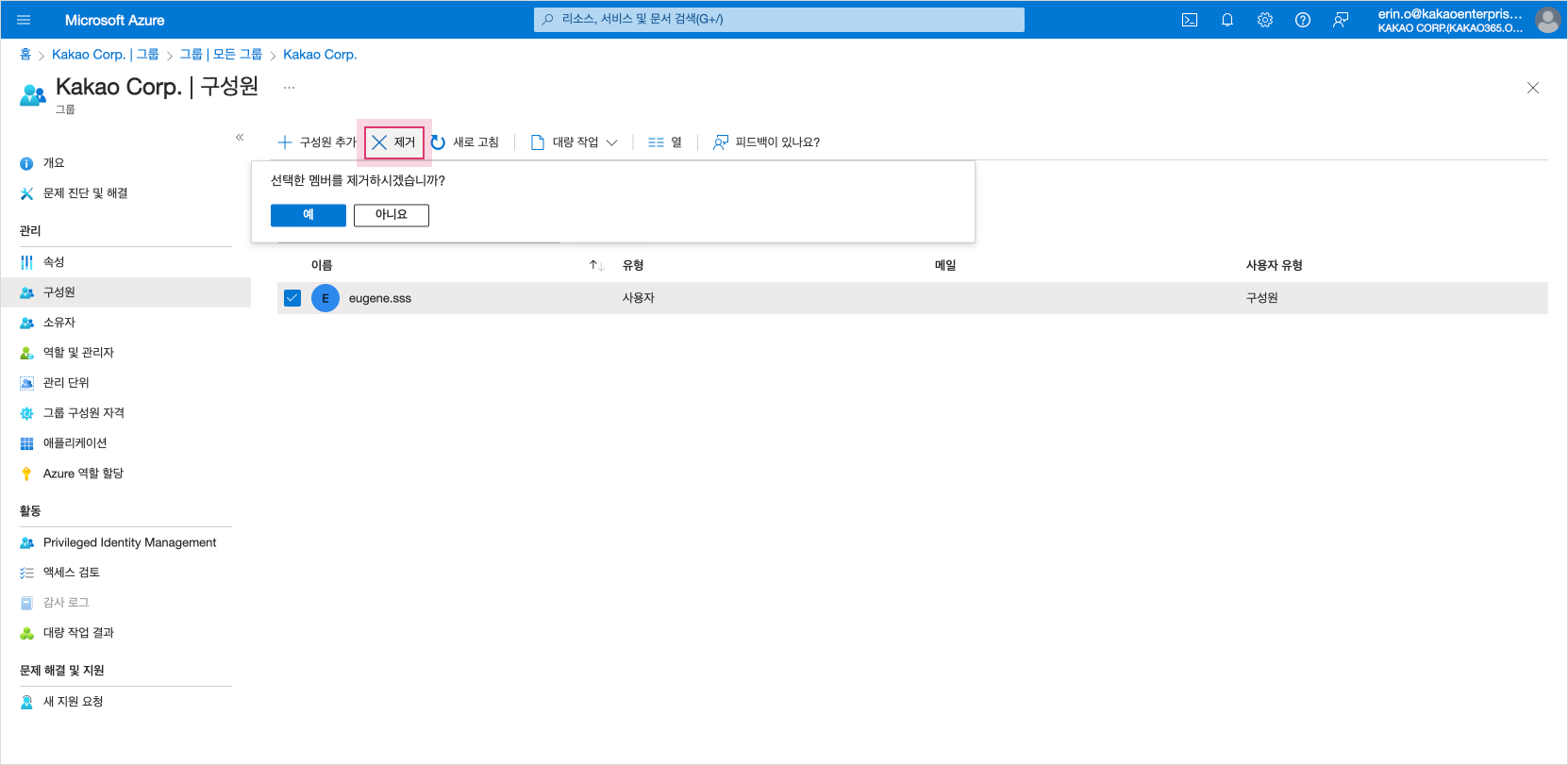 Delete Microsoft Entra ID User
Delete Microsoft Entra ID User
Step 2. Delete User in KakaoCloud Organization
-
Log in to the KakaoCloud console with the Org Owner account.
-
Select the Organization Management icon > User menu.
-
Check the user you want to delete and select Delete User.
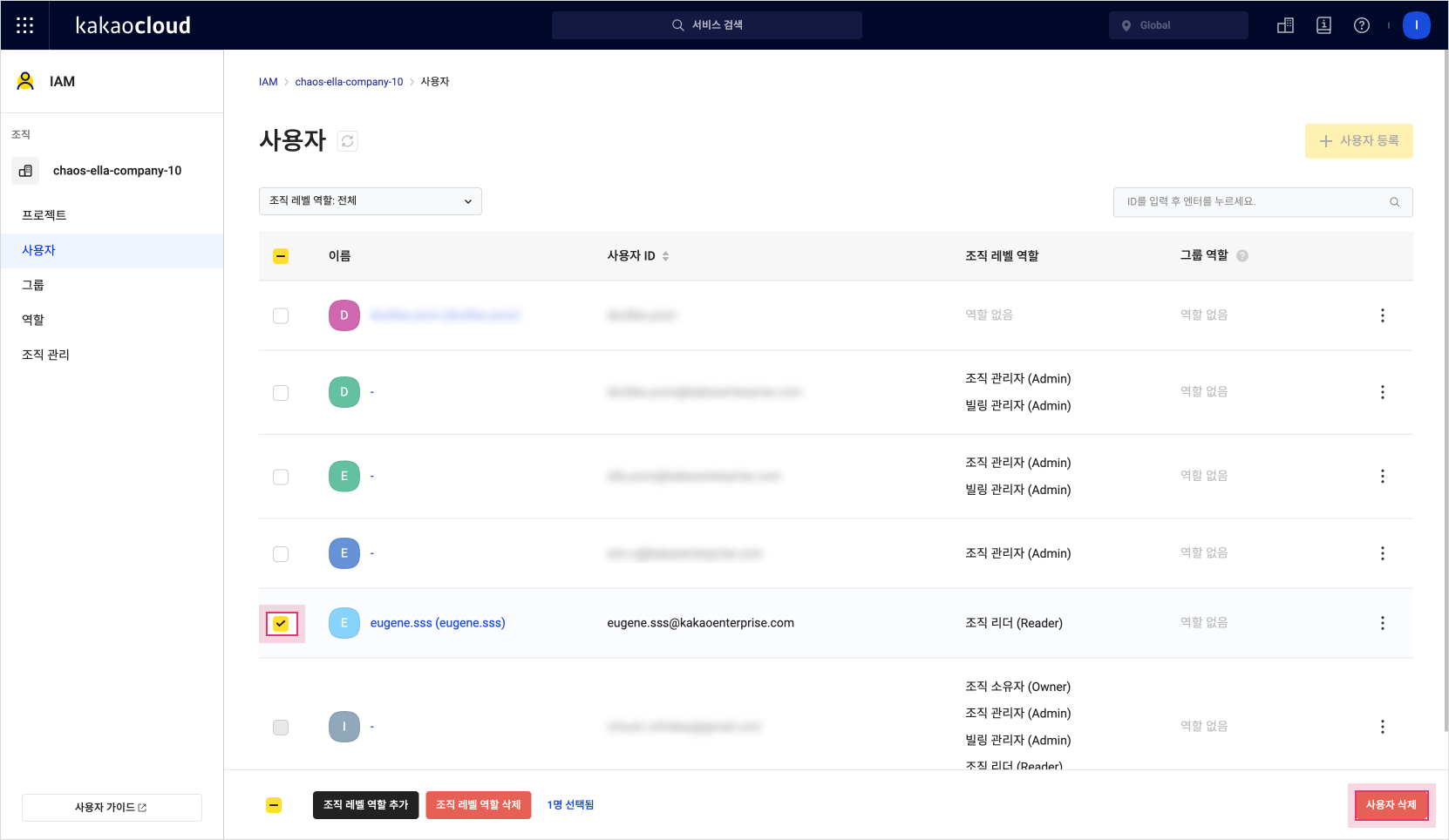 Delete user
Delete user -
In the pop-up window that appears, enter the phrase "Delete user from organization" and select Delete to complete deleting the user within the organization.
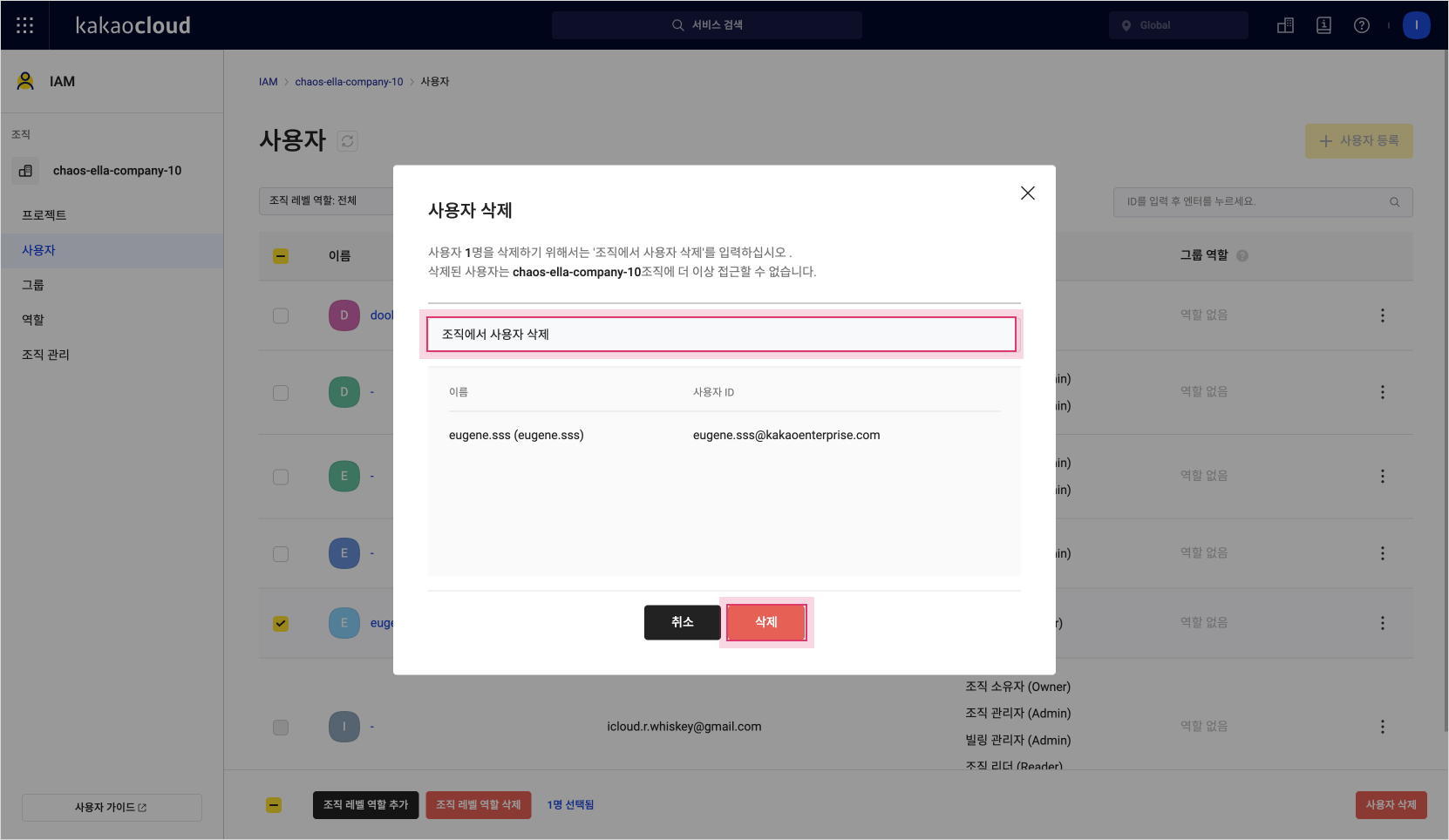 User deletion pop-up
User deletion pop-up
Step 3. Confirm user deletion
If you log out of the KakaoCloud console again and try to log in by entering the deleted user account, you will see the error message below and be unable to log in.
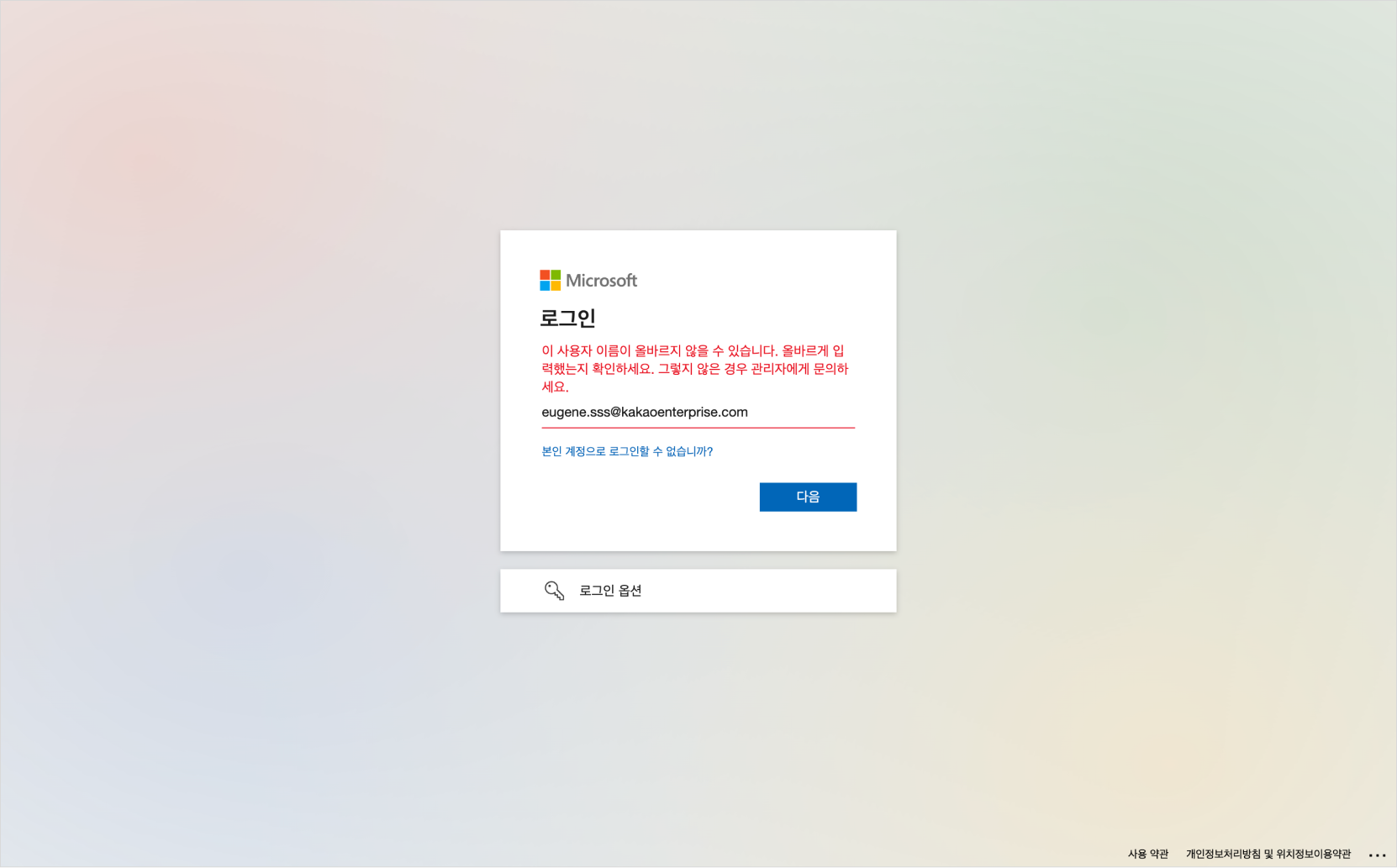 Unable to log in as a deleted user
Unable to log in as a deleted user