Bucket CORS policy
Configure bucket CORS policy
CORS (Cross-Origin Resource Sharing) is a feature that allows web applications running on a specific domain to access resources on a different domain. In Object Storage, you can configure CORS policies for a bucket to allow responses only to specified domains. A maximum of 10 CORS policies can be set per bucket.
The configuration method for a CORS policy in Object Storage is as follows.
If the detailed rules are not followed when setting a CORS policy, a 400 Bad Request error may occur.
Sequence of priority for CORS policy
When multiple CORS policies are entered and a request is received, the order of comparison is as follows:
- Policies are evaluated in the order they were entered.
- The first policy that matches the request’s origin is used.
- For the first matching origin, the allowed methods and allowed headers are checked and a response is generated.
Composition of policy details
The components of a CORS policy are as follows:
| Field | Description |
|---|---|
| allowed_origins | Specifies the origins allowed to access the bucket's CORS. - Example: https://example.com |
| allowed_methods | Specifies the HTTP methods allowed for CORS with the bucket. - Returned in the Access-Control-Allow-Methods header in response to a successful preflight request |
| allowed_headers | Specifies the headers allowed for CORS with the bucket. - Returned in the Access-Control-Allow-Headers header in response to a successful preflight request |
| expose_headers | Lists the headers that can be exposed to the browser in the Access-Control-Expose-Headers response |
| max_age_seconds | Time in seconds to cache the preflight OPTIONS request response - Returned in the Access-Control-Max-Age header in response to a preflight request |
Detailed rules for each CORS component
Each CORS component must comply with specific rules.
allowed_origins
Specifies the origins allowed to access the resource. Required field.
- Case-sensitive
- Allows only one wildcard (*) per origin
- Valid:
console.*.kakao.io - Invalid:
*.*.kakao.io - Maximum length per origin: 200 characters
- Maximum of 10 origins per policy
- Allowed characters:
- Alphanumeric
- Colon (:)
- Forward slash (/)
- Dot (.)
- Wildcard (*)
- Regex:
^[*a-zA-Z0-9:/.-]*$ - Cannot mix with disallowed characters
- Max 10 entries per CORS object
allowed_methods
Specifies the allowed HTTP methods. Required field.
- Case-sensitive
- Only uppercase is valid; lowercase results in 400 Bad Request
- Allowed characters:
- Uppercase letters
- Wildcard (*)
- Regex:
^[*A-Z]*$ - Duplicate entries are allowed
- Valid values: GET, PUT, POST, DELETE, HEAD, * (wildcard covers the five listed methods)
- Max 5 methods per CORS object
allowed_headers
Specifies the headers allowed by the browser (default exposed). Required field.
- Case-sensitive
- Allows one wildcard (*)
- Max length per entry: 200 characters
- Allowed characters:
- Alphanumeric
- Dash (-)
- Wildcard (*)
- Regex:
^[a-zA-Z\d-*]+$ - Max 10 entries per CORS object
expose_headers
Specifies the headers that are not exposed by default in the browser. Required field.
- Max length per entry: 200 characters
- Allowed characters:
- Alphanumeric
- Dash (-)
- Wildcard (*)
- Regex:
^[a-zA-Z0-9-]*$ - Max 10 entries per CORS object
- For headers like
x-account-meta-*,x-container-meta-*,x-object-meta-*, the exact meta name must be specified instead of using*
max_age_seconds
Indicates the cache duration for the preflight request result. Optional field.
- Must be an integer greater than or equal to 0
- Max value: 86400 (1 day)
- Default: 0 if not specified
HTTP header list
The following HTTP headers are used in CORS request and response. For more information, refer to:
| Header | Description |
|---|---|
| Accept | Specifies accepted MIME types for the client |
| Accept-Ranges | Indicates partial request support |
| Content-Disposition | Indicates how content should be displayed (inline or attachment) |
| Content-Encoding | Specifies compression used |
| Content-Length | Size of response body in bytes |
| Content-Range | Indicates the range of partial content |
| Content-Type | Media type of the resource |
| ETag | Identifier for a specific version of a resource |
| Expect | Indicates expectations from the server |
| Host | Specifies domain and port number |
| Last-Modified | Last modified date and time of the resource |
| Origin | Indicates where fetch request originated from |
| Range | Requests a specific portion of a resource |
| Referer | Specifies the source of the request |
| Transfer-Encoding | Encoding for safely transmitting entity |
| X-Account-Meta-* | Account-level metadata |
| X-Auth-Token | Authentication token |
| X-Container-Bytes-Used | Total used bytes in container |
| X-Container-Meta-* | Container-level metadata |
| X-Container-Object-Count | Number of objects in container |
| X-Object-Manifest | Manifest for segmented large objects |
| X-Object-Meta-* | Object-level metadata |
| X-Openstack-Request-Id | Unique request transaction ID |
| X-Static-Large-Object | Indicates static large object manifest |
| X-Subject-Token | Token returned upon successful authentication |
| X-Timestamp | UNIX epoch timestamp of object creation |
| X-Trans-Id | Unique transaction ID |
| X-Trans-Id-Extra | Extra information for debugging large transactions |
Configure bucket CORS policy
CORS (Cross-Origin Resource Sharing) allows web apps on one domain to access resources on another.
In Object Storage, a CORS policy can be set on a bucket to restrict responses to specified domains. Only users with the storage admin role can configure CORS policies for individual buckets. By default, the origin in a CORS policy denies access from external domains.
Follow the steps below to configure a bucket CORS policy.
Set new CORS policy
You can configure a new CORS policy.
Only users with the storage admin role can configure bucket CORS policies.
-
Go to KakaoCloud console > Beyond Storage Service > Object Storage.
-
Select the bucket from the Standard bucket menu.
-
Select the Permission tab, then go to the CORS tab, input the policy in the JSON Editor, and select [OK].
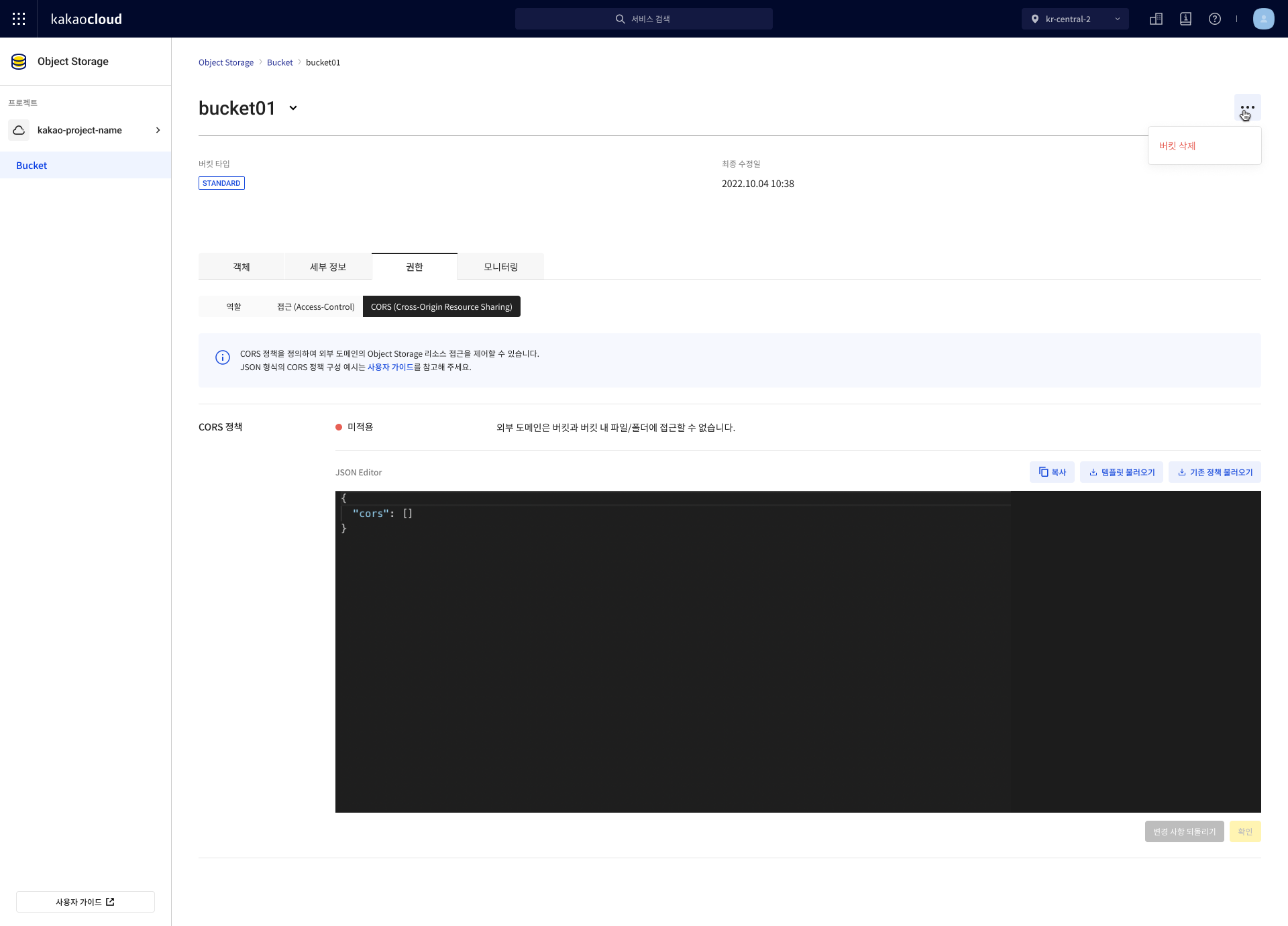
Load existing template
You can load an existing template. The default code is automatically filled in, applying a default CORS policy template.
Edit the default code as needed. Using it as-is may result in unintended CORS behavior.
-
Go to KakaoCloud console > Beyond Storage Service > Object Storage.
-
Select the target bucket from the Standard bucket menu.
-
Select the Permission tab, then the CORS tab, and select the [Load template] button.
Default code for loading template{
"cors": [
{
"allowed_origins": [
"http://example.com",
"http://example.com:8080",
"https://example.com",
"http://*.example.com"
],
"allowed_methods": [
"GET",
"HEAD"
],
"allowed_headers": [
"X-Auth-Token"
],
"expose_headers": [
"Access-Control-Allow-Origin"
],
"max_age_seconds": 0
}
]
}
Load existing policy
You can load a CORS policy applied to another bucket within the same project and edit it.
You must have the storage admin role for the source bucket, and that bucket must already have a CORS policy configured.
-
Go to KakaoCloud console > Beyond Storage Service > Object Storage.
-
Select the bucket from the Standard bucket menu.
-
Select the Permission tab, then the CORS tab, and select the [Load existing policy] button.
-
In the popup window, input the information and select [Load].
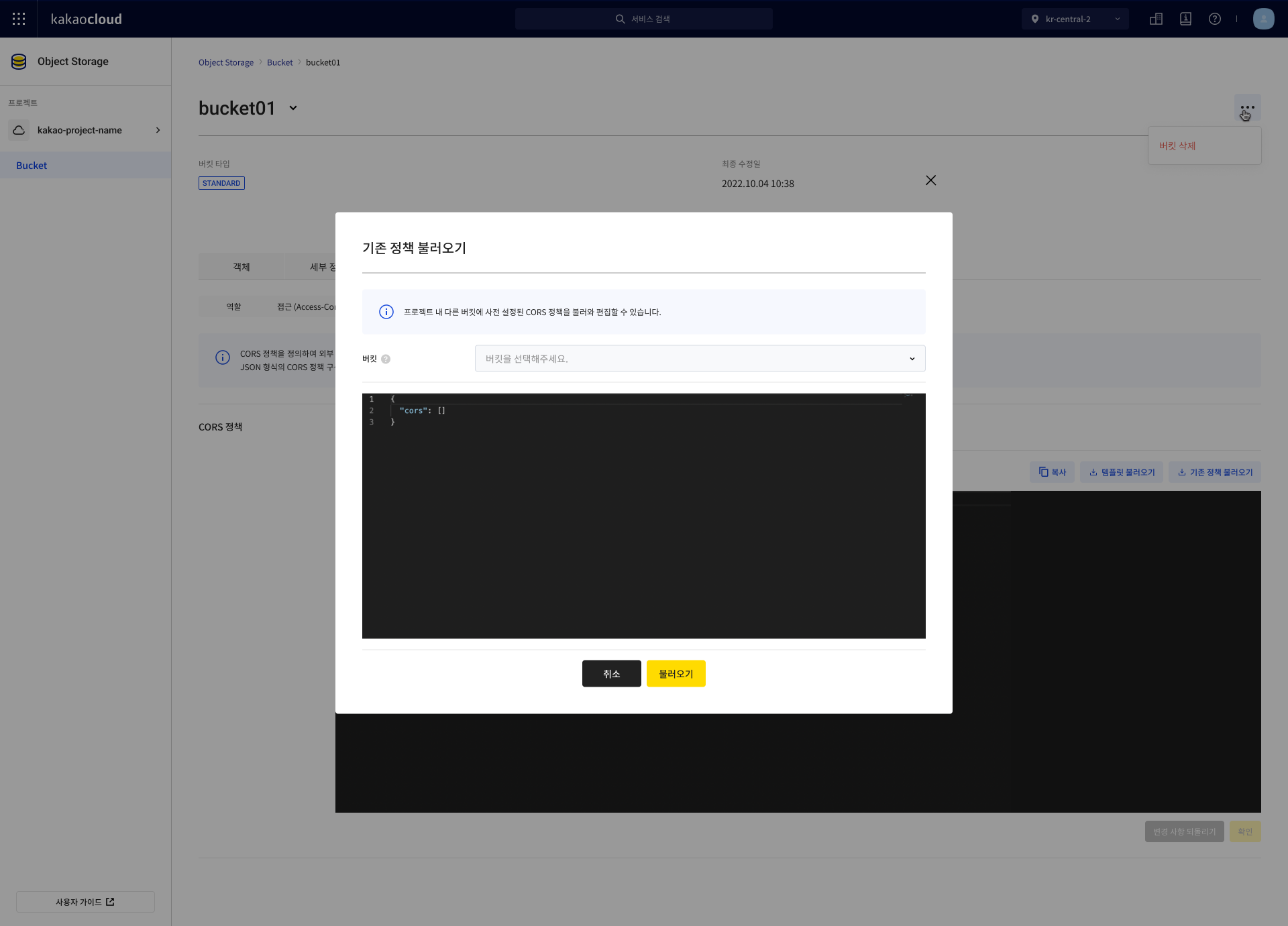
Apply policy
Apply the CORS policy to a bucket.
- Go to KakaoCloud console > Beyond Storage Service > Object Storage.
- Select the target bucket from the Standard bucket menu.
- In the Permission tab, open the CORS tab, enter the policy in the JSON Editor, and select [OK].
- Select [Undo changes] to revert to the previous state.
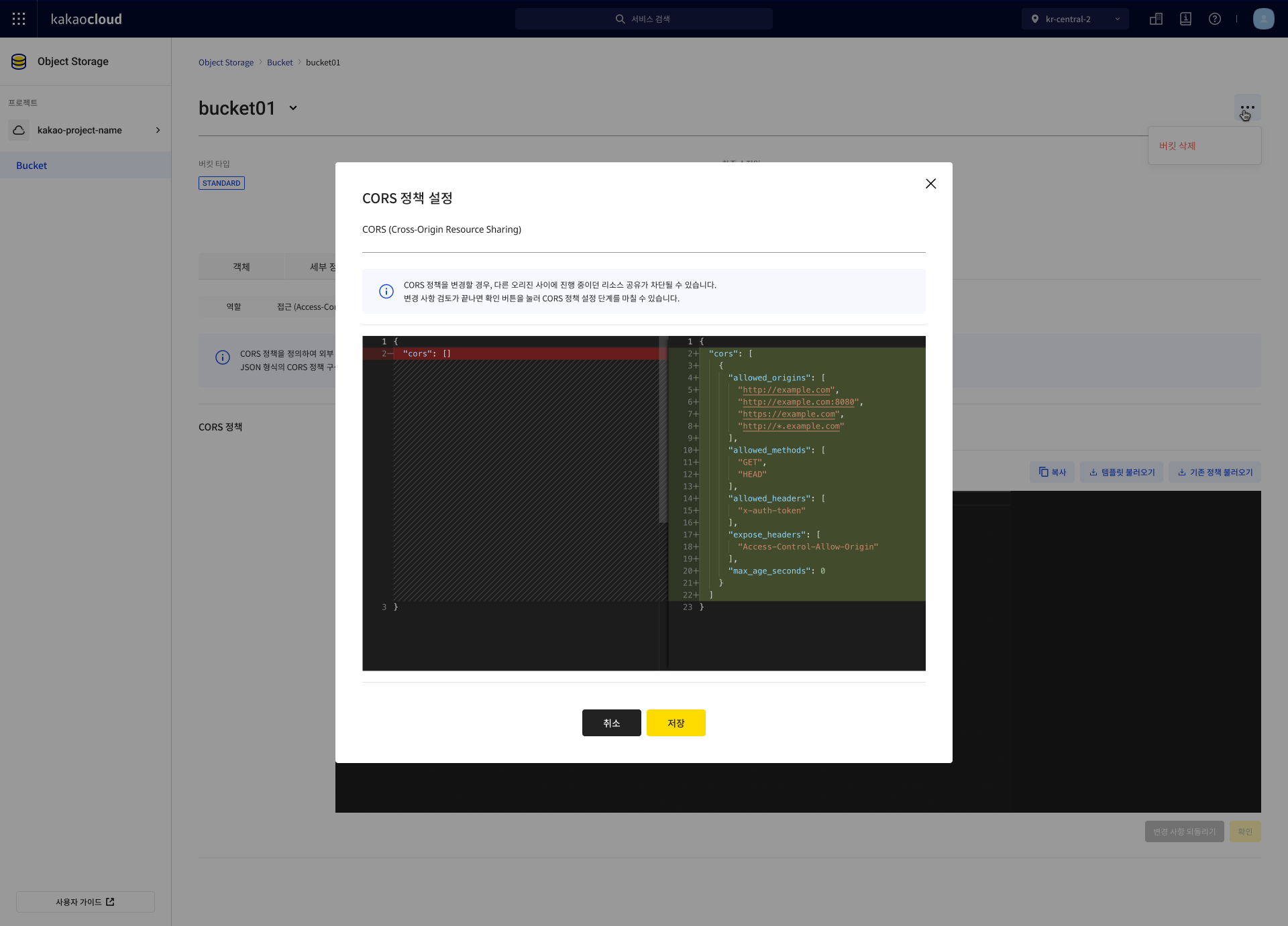
- In the CORS policy setting popup, review the changes and select [OK].
Delete policy
You can delete an applied CORS policy. Deleting the policy will block ongoing resource sharing between origins.
-
Go to KakaoCloud console > Beyond Storage Service > Object Storage.
-
Select the bucket from the Standard bucket menu.
-
Select the Permission tab, then the CORS tab, and check if a CORS policy is applied.
-
In the Delete CORS policy popup, select the [Delete] button.
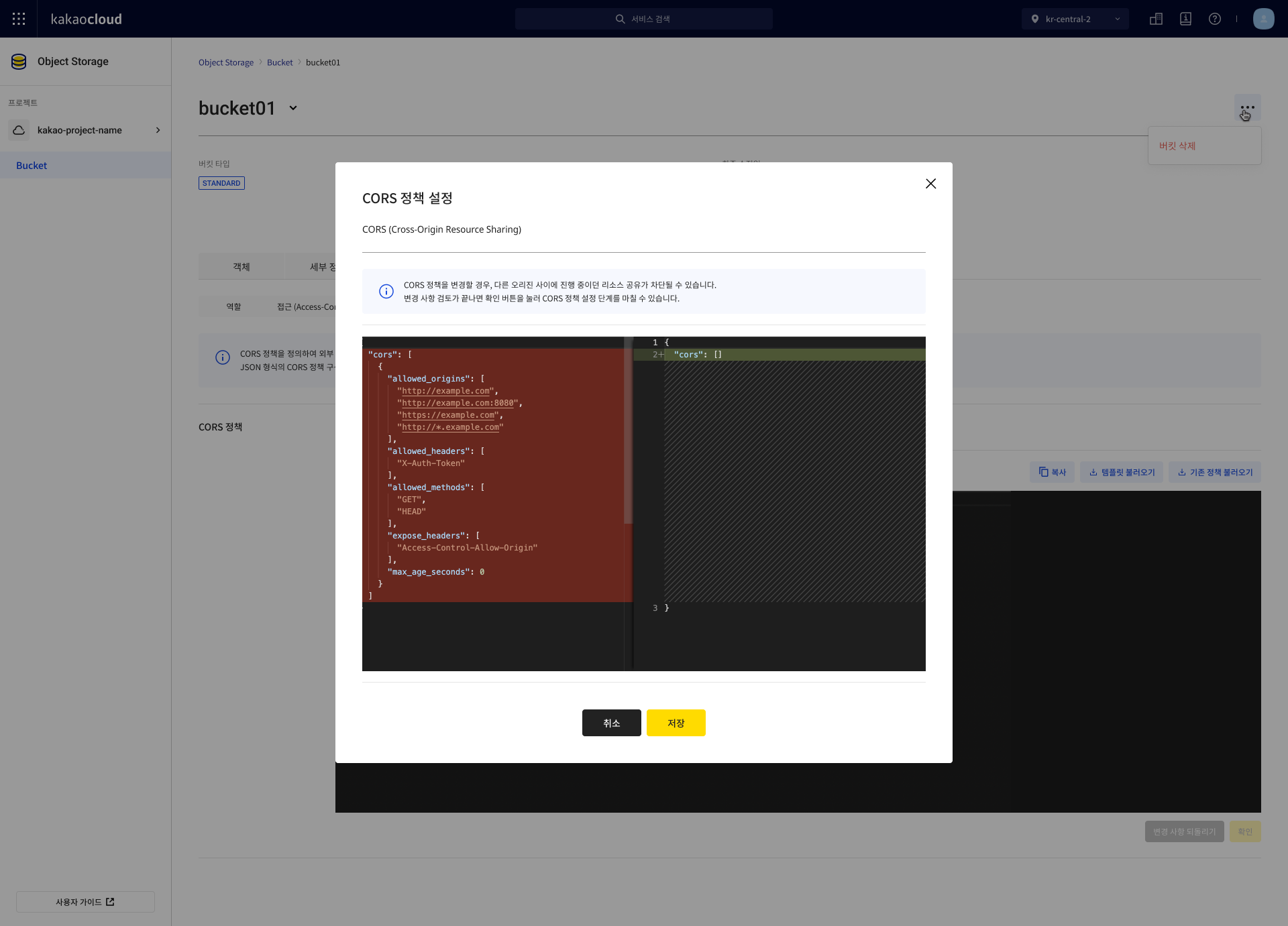
-
Confirm that the CORS policy status is now Not applied.
Examples of bucket CORS policy
CORS policy must be in JSON format and supports up to 10 rules. You can use custom domains such as example1.com instead of direct endpoint access. For detailed configuration, refer to Configure bucket CORS policy.
The following example defines two CORS rules.
| Rule | Description |
|---|---|
| Rule 1 | Allows cross-origin GET, HEAD, and PUT requests from https://example.com and http://*.example.com- Only X-Auth-Token is allowed for preflight OPTIONS via Access-Control-Request-Headers |
| Rule 2 | Allows cross-origin POST requests from any origin- * (wildcard) allows all origins |
{
"cors": [
{
"allowed_origins": [
"https://example.com",
"http://*.example.com"
],
"allowed_methods": [
"GET",
"HEAD",
"PUT"
],
"allowed_headers": [
"X-Auth-Token"
],
"expose_headers": [
"Access-Control-Allow-Origin"
],
"max_age_seconds": 5
},
{
"allowed_origins": [
"*"
],
"allowed_methods": [
"POST"
],
"allowed_headers": [ ],
"expose_headers": [ ]
}
]
}